Last article, We had covered Kubernetes Deployment Using Helm [Part 1]
In this article, We are going to perform Automatic Deploy to Kubernetes using Helm and GitLab CI CD Pipeline with Auto restart Kubernetes Pod on same version.
Also, You can deploy to Dev, Test, UAT and Production Environment within same GitLab CI YML.
Table of Contents
Introduction
If you want to create CI CD pipeline to Auto deployment to Kubernetes using GitLab and Helm with auto restart pod
Prerequisite
- Kubernetes Cluster Access
- Pre-Installed GitLab Runner and GitLab Runner Registration
If you have not setup Kubernetes Cluster , Follow below articles to setup.
9 Steps to Setup Kubernetes on AWS using KOPS
1. Install Helm on GitLab Runner Instance
First, Install the GitLab Runner on GitLab Runner Instance where you are Registering GitLab Runner of your project Repositories
sudo wget https://get.helm.sh/helm-v2.16.8-linux-amd64.tar.gz
sudo tar -zxvf helm-v3.0.0-linux-amd64.tar.gz
sudo mv linux-amd64/helm /usr/local/bin/helm
sudo snap install helm --classic
2. Encode Kube config into Base64
Login to Kubernetes master/management node and encode kube config into base 64
ls -a
cd .kube
cat config | base64
Copy the output in Notepad
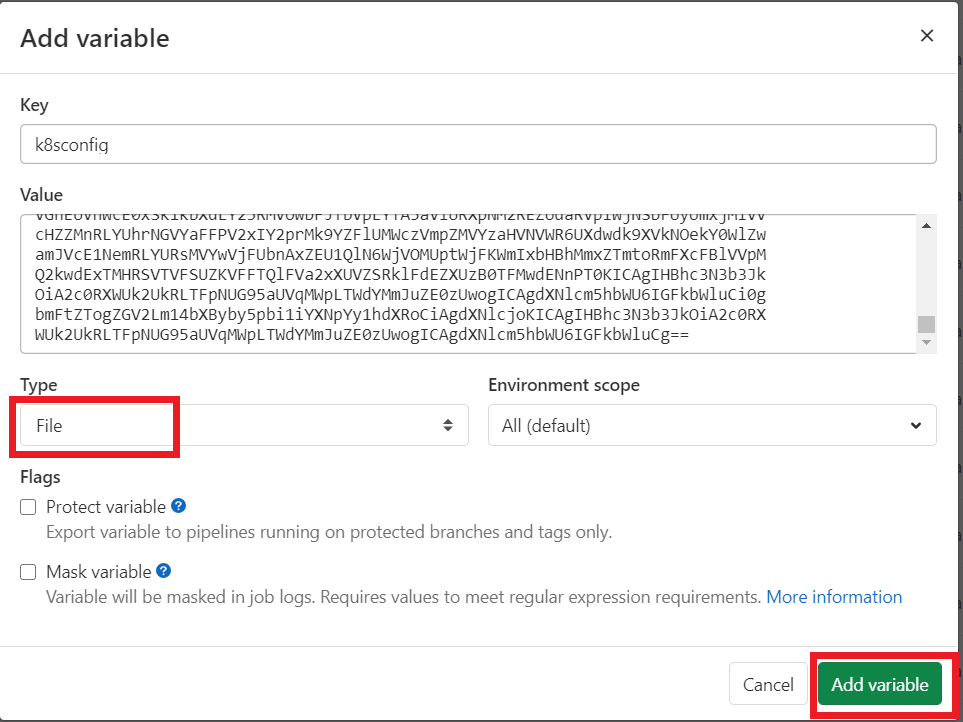
Now Login to your GitLab Server, Create a variable in named “k8sconfig” in your GitLab Project , type should be as File and click on Add variable
3. Create file named “config_k8s” in GitLab Runner
sudo nano config_k8s
4. Deploy to Kubernetes using Helm and GitLab
open your project’s .gitlab-ci.yml , add below lines in deploy stage.
deploy_k8s:
stage: deploy
when: manual
image: Docker_ECR_Image_URI/${SERVICE_TEST}:latest
before_script:
- sudo mkdir -p /etc/deploy
- cat ${config_k8s} | base64 -d > config_test
- sudo cp -r config_dev /etc/deploy/config
- kubectl config set-cluster ${K8S_CLUSTER_NAME} --server="${SERVER}"
- kubectl config set clusters.${K8S_CLUSTER_NAME}.certificate-authority-data ${CERTIFICATE_AUTHORITY_DATA}
- kubectl config set-credentials gitlab-runner --token="${USER_TOKEN}"
- kubectl config set-context ${K8S_CLUSTER_NAME} --cluster=${K8S_CLUSTER_NAME} --user=gitlab-runner
- kubectl config use-context ${K8S_CLUSTER_NAME}
- helm init --client-only
- helm repo add stable https://kubernetes-charts.storage.googleapis.com/
- helm repo add incubator https://kubernetes-charts-incubator.storage.googleapis.com/
- helm repo update
script:
- export API_VERSION=$(grep "appVersion" ${SERVICE_TEST}/Chart.yaml | cut -d '"' -f2)
- export RELEASE_NAME="${SERVICE_TEST}-v${API_VERSION/./-}"
- export DEPLOYS=$(helm ls | grep $RELEASE_NAME | wc -l)
- if [ ${DEPLOYS} -eq 0 ]; then helm install --name=${RELEASE_NAME} ${SERVICE_TEST}; else helm upgrade --recreate-pods ${RELEASE_NAME} ${SERVICE_TEST}; fi5. Setup GitLab Environment Variables
Add Below Project’s microservice and Kubernetes clusters value in your GitLab Project Environment Variables
Navigating to Settings there is one option CI/CD inside this click on Expand of Variables.
- SERVICE_TEST : Project’s Micro Service Name
- K8S_CLUSTER_NAME: Kubernetes Cluster ( for ex. dev.fosstechnix.com)
- SERVER: Kubernetes Server URL ( for ex: https://api.dev.fosstechnix.com)
- CERTIFICATE_AUTHORITY_DATA : ( Kubernetes Cluster certificate-authority-data value)
- USER_TOKEN: Kubernetes Cluster’s Secrets
you can get USER_TOKEN using below command and get the token value.
kubectl describe secrets service-account-name -n namespace
Conclusion
In this article, We have covered Automatic Deploy to Kubernetes using Helm and GitLab CI CD Pipeline.
Related Articles
7 Steps for GitLab Runner Registration
Reference
