In this Article we are going to discuss about Installing Istio Service Mesh with Observability Add-ons on Ubuntu 24.04.
Istio is one of the most powerful service mesh technologies available today. It provides a robust way to manage microservices traffic, security, and observability. In this guide, you’ll learn how to set up Istio Service Mesh on Ubuntu 24.04, and deploy observability tools like Jaeger, Prometheus, Grafana, and Kiali. You’ll also run a sample microservices app and expose it using port-forwarding.
Table of Contents
Prerequisites
- Ubuntu 24.04 EC2 instance (recommended: t2.xlarge or better)
- At least 8 GB RAM and 4 CPUs
- Internet access
- A security group with open ports:
- 22 (SSH)
- 8080, 16686, 20001, etc. for observability tools
- 30000-32767 if using NodePorts
- Minikube and Kubectl
Step by Step Guide Installing Istio Service Mesh with Observability Add-ons on Ubuntu 24.04 LTS
Step #1:Download and Set Up Istio CLI
1. Download latest Istio release:
curl -L https://istio.io/downloadIstio | ISTIO_VERSION=1.26.0 sh -
cd istio-1.26.0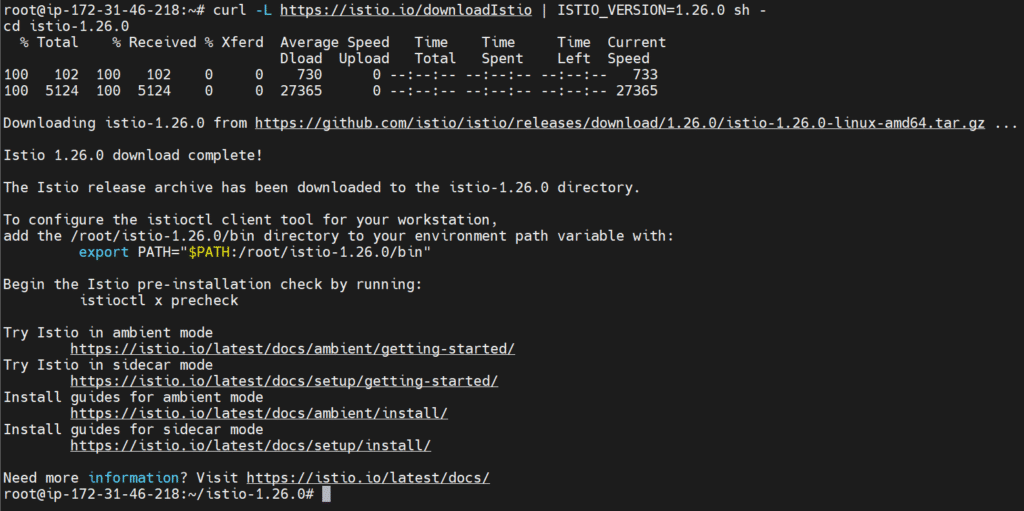
(Replace 1.26.0 with the latest version if needed.)
2. Add istioctl to your path:
export PATH="$PWD/bin:$PATH"
To make it permanent:
echo 'export PATH="$PWD/bin:$PATH"' >> ~/.bashrc
source ~/.bashrc
Step #2:Install Istio on Kubernetes
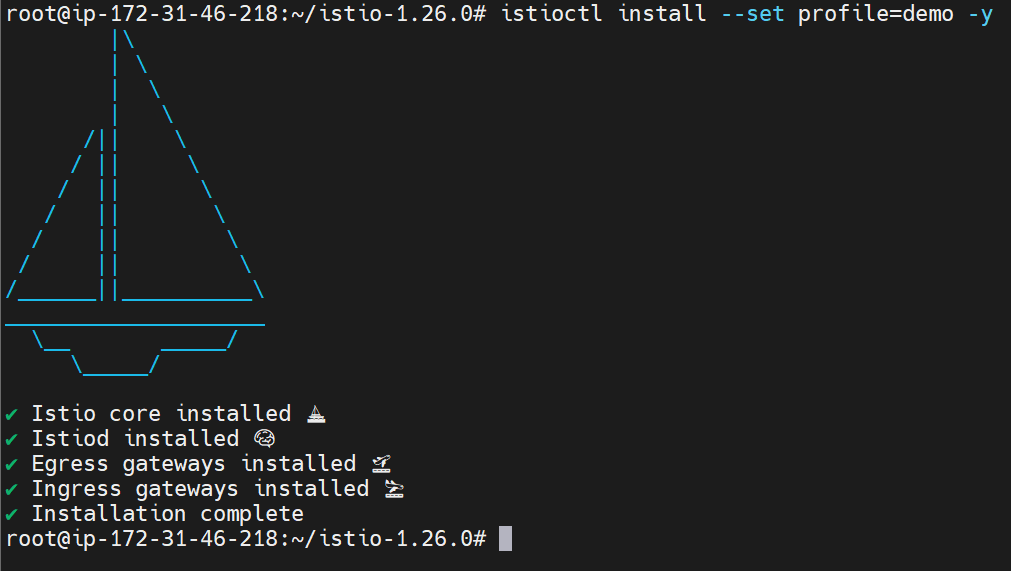
Install Istio control plane:
istioctl install --set profile=demo -y
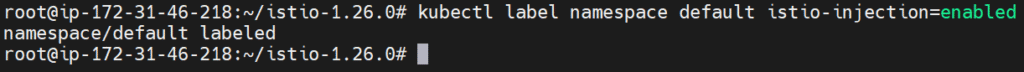
Label the default namespace for automatic Envoy injection:
kubectl label namespace default istio-injection=enabled
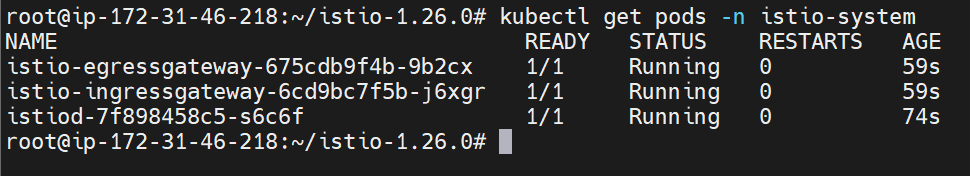
Verify installation:
kubectl get pods -n istio-system
Step #3:Deploy Sample Microservices App
Clone the microservices demo:
git clone https://github.com/GoogleCloudPlatform/microservices-demo.git
cd microservices-demo/release

Apply the deployment:
kubectl apply -f kubernetes-manifests.yaml

Check that the pods are running:
kubectl get pods
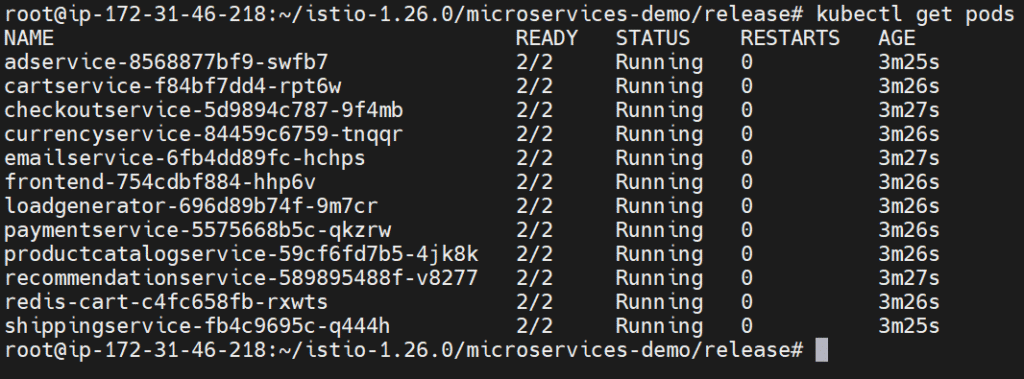
Step #4:Enable Istio Observability Add-ons
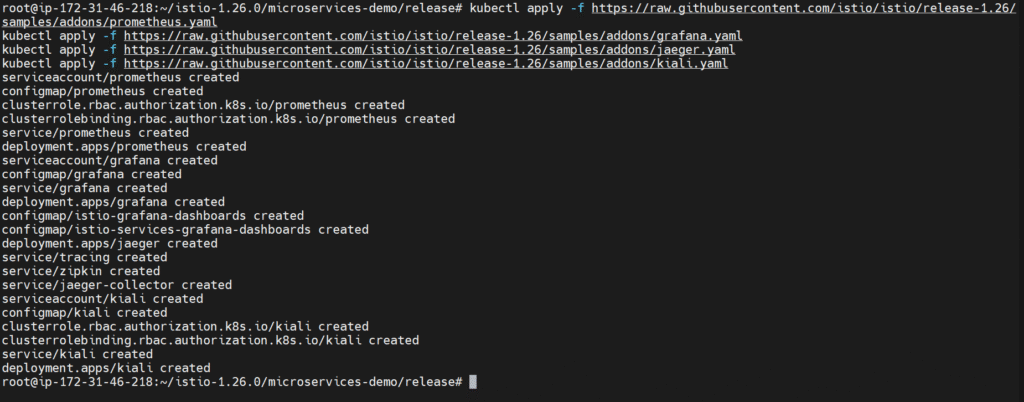
Apply add-ons:
kubectl apply -f https://raw.githubusercontent.com/istio/istio/release-1.26/samples/addons/prometheus.yaml
kubectl apply -f https://raw.githubusercontent.com/istio/istio/release-1.26/samples/addons/grafana.yaml
kubectl apply -f https://raw.githubusercontent.com/istio/istio/release-1.26/samples/addons/jaeger.yaml
kubectl apply -f https://raw.githubusercontent.com/istio/istio/release-1.26/samples/addons/kiali.yaml
Create service for Jaeger UI (if needed):
# jaeger-ui-service.yaml
apiVersion: v1
kind: Service
metadata:
name: jaeger
namespace: istio-system
spec:
selector:
app: jaeger
ports:
- protocol: TCP
port: 16686
targetPort: 16686
Apply it:
kubectl apply -f jaeger-ui-service.yaml

Now port-forward:
kubectl port-forward svc/jaeger -n istio-system --address 0.0.0.0 16686:16686
kubectl port-forward svc/prometheus -n istio-system --address 0.0.0.0 9090:9090
kubectl port-forward svc/grafana -n istio-system --address 0.0.0.0 3000:3000
kubectl port-forward svc/kiali -n istio-system --address 0.0.0.0 20001:20001
Now open in your browser (replace <EC2-IP>):
Jaeger: http://<EC2-IP>:16686
Prometheus: http://<EC2-IP>:9090

Grafana: http://<EC2-IP>:3000

Kiali: http://<EC2-IP>:20001
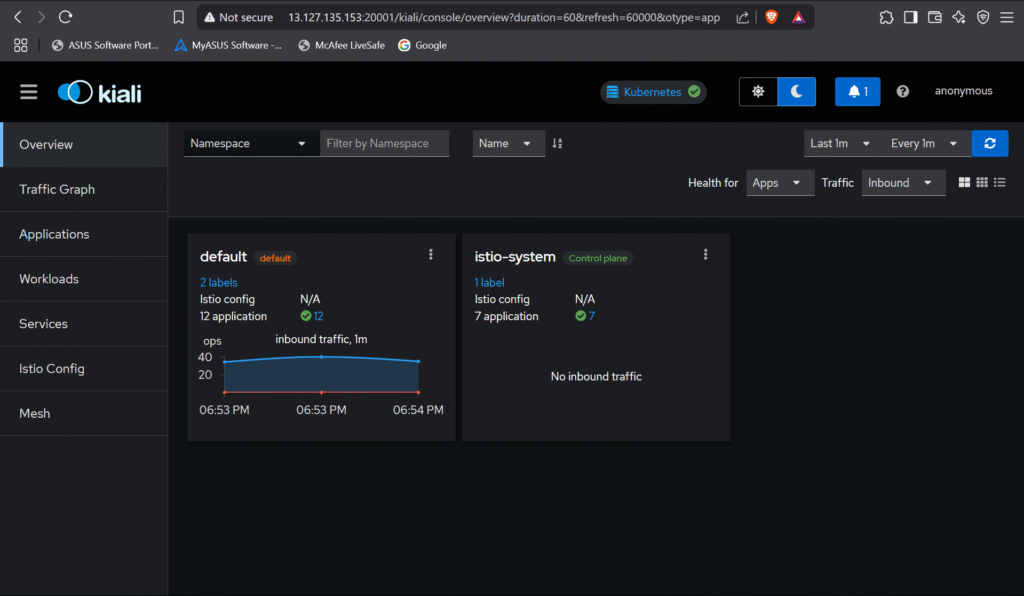
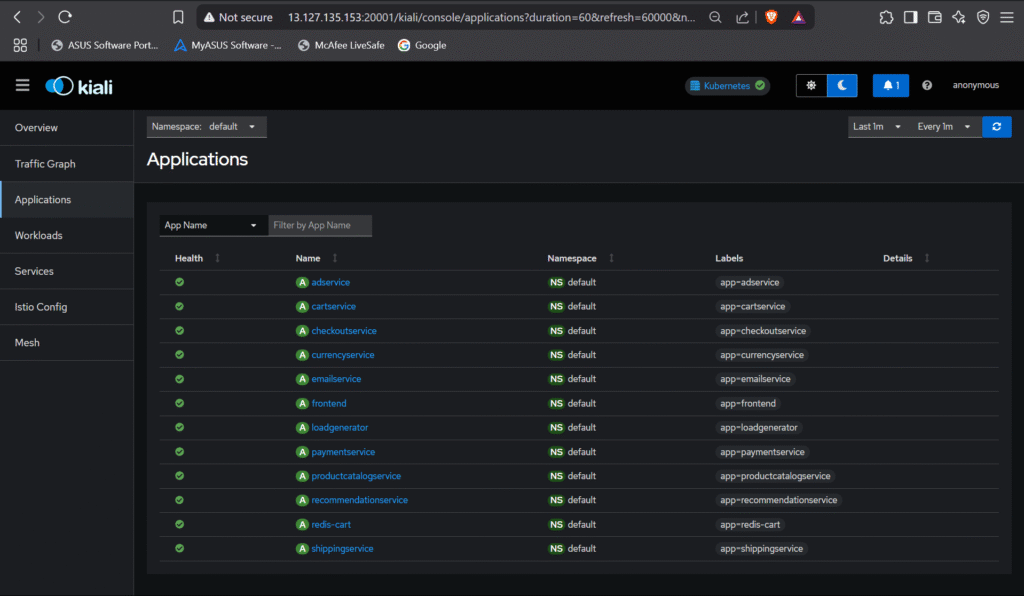
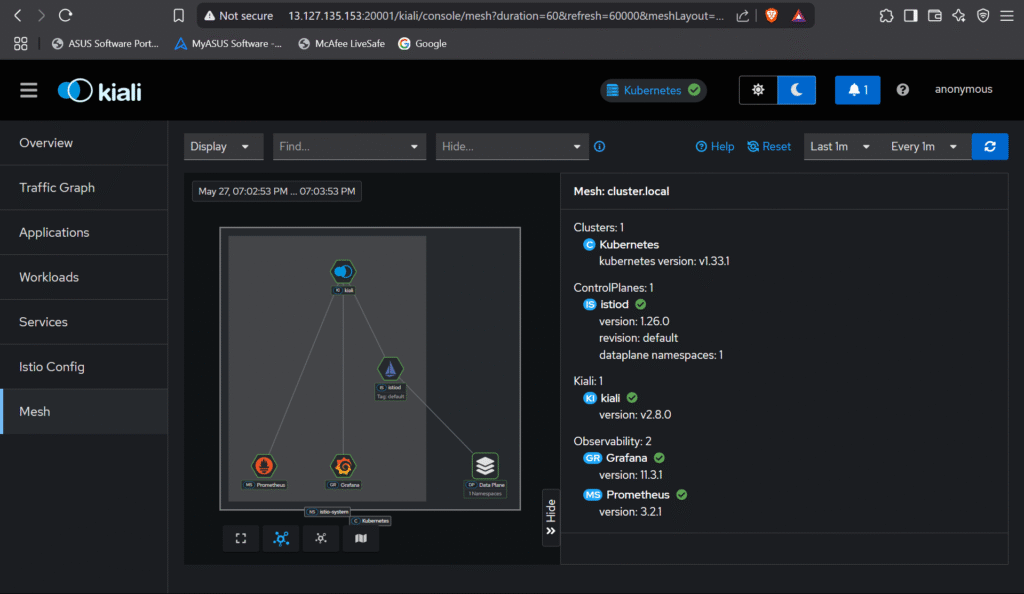
Step #5:Verify Service Mesh Working
Use kiali to visualize the service mesh topology and traffic flow.
Step #6:Access the Application
Access the Application by using the port-forward:
kubectl port-forward svc/frontend-external --address 0.0.0.0 8080:80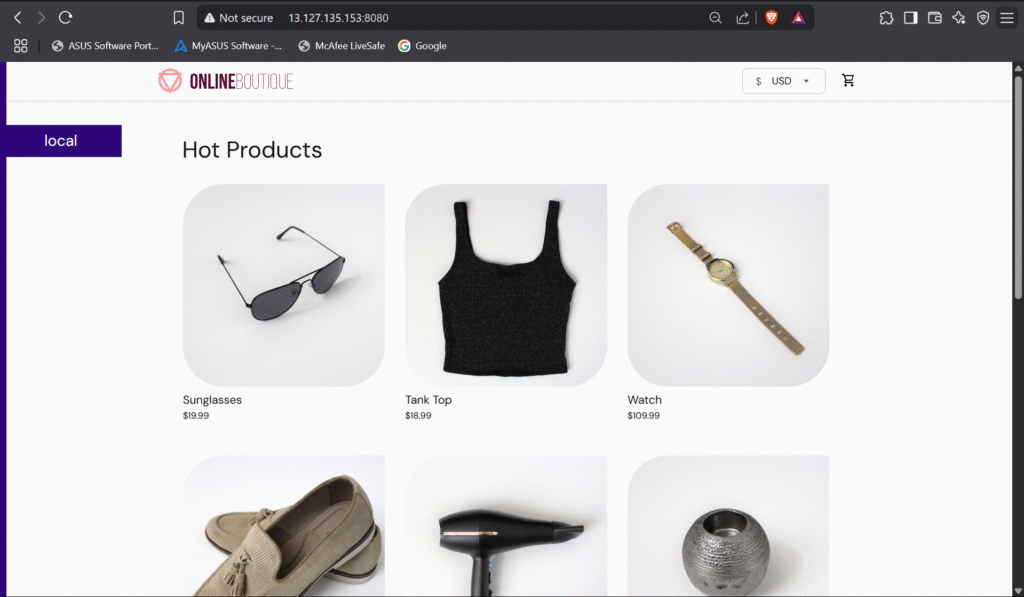
Conclusion:
Monitoring your deployed application with Istio’s observability tools provides deep insights into the health, performance, and behavior of your microservices. By integrating Prometheus for metrics collection, Grafana for visualization, Jaeger for distributed tracing, and Kiali for real-time service mesh visualization, you gain a powerful, unified observability stack. This setup not only helps you troubleshoot issues quickly but also enables proactive performance tuning and infrastructure optimization. Whether you’re running in development or production, Istio’s observability features are essential for maintaining a resilient and transparent Kubernetes environment.
Related Articles:
Kubernetes Traefik Ingress LetsEncrypt – cert-manager, TLS
Reference:
