In this article, we will explore the process of setting up an AWS Site-to-Site Virtual Private Network (VPN) to establish secure communication between your on-premises network and AWS resources.
Table of Contents
What is AWS Site-to-Site VPN?
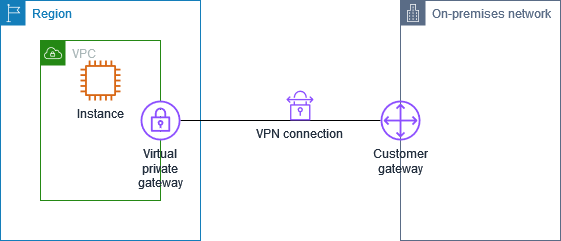
AWS Site-to-Site VPN is a secure way to connect your on-premises network (like your office network or data center) to your AWS cloud resources. It’s like building a private tunnel through the internet between your office and AWS, ensuring that your data travels safely and privately.
Example:
Imagine you have a small business with an office network where you store important files and run applications. You also use AWS cloud services like storage and databases. With AWS Site-to-Site VPN, you can securely link your office network to AWS. It’s like having a virtual extension cord that lets your office network access resources in AWS securely, just as if they were all in the same physical location.
Components of VPN
- VPN Tunnel: Secure pathway for data between locations, like a virtual pipeline. Example: Connecting to work from home using VPN.
- Virtual Private Gateway (VPG): Entry point to cloud network, manages VPN connections. Example: AWS VPG for secure connection to VPCs.
- Customer Gateway (CGW): Represents on-premises network in VPN, endpoint for VPN connections. Example: Office router connecting to AWS via VPN.
- Site-to-Site VPN Connection: Secure link between separate networks, like a virtual bridge. Example: Site-to-Site VPN between office network and AWS VPC.
- VPN Configuration: Settings for VPN connections, includes encryption, authentication, and routing details. Example: Configuring VPN parameters on routers for secure communication.
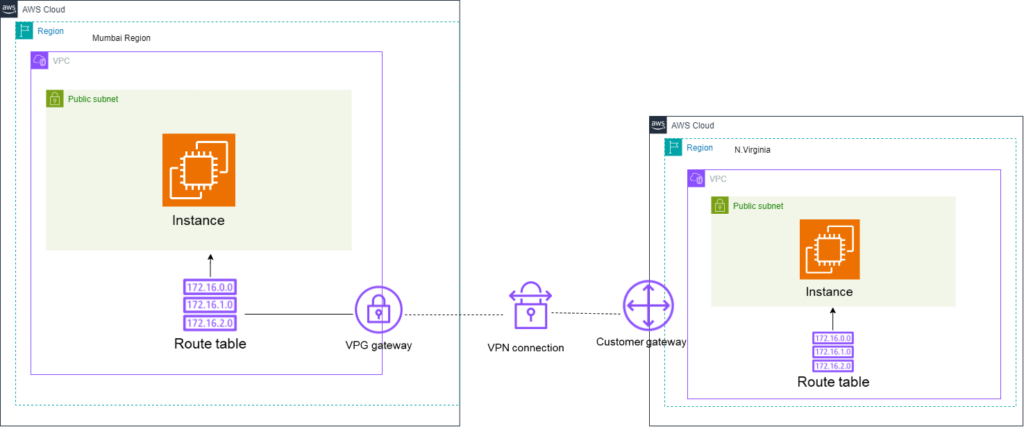
Architecture of Site-to-Site VPN
What is IPSec?
IPSec: Enhancing Network Security
IPSec is a network protocol suite used in VPNs to secure data transmission over IP networks. It authenticates and encrypts data packets, ensuring:
- Confidentiality: Encrypts data to prevent unauthorized access.
- Integrity: Ensures data remains unchanged during transmission.
- Authentication: Verifies sender and receiver identities.
- Anti-Replay: Prevents attackers from reusing captured packets.
IPSec creates encrypted tunnels for secure data transfer, bolstering network security.
Benefits of using AWS Site-to-Site VPN
- AWS Site-to-Site VPN encrypts all data exchanged between your on-premises network and AWS, ensuring secure transmission and protecting sensitive information from unauthorized access.
- By seamlessly connecting your on-premises network to the AWS cloud, organizations can establish a hybrid architecture where resources can securely interact with AWS services.
- Amazon CloudWatch Logs provides comprehensive monitoring, storage, and access to log files related to AWS Client VPN connections, offering valuable insights into network activity.
- Implementing AWS Site-to-Site VPN eliminates the need for costly leased lines or hardware-based VPN equipment, resulting in reduced expenses associated with maintaining traditional networking infrastructure.
Importance of securely connecting on-premises network to AWS VPN
- Many companies store and analyze sensitive data in on-premises networks. By establishing a secure connection to AWS, you can securely transfer data to and from the cloud.
- Certain industries and regulatory regimes impose severe security and compliance requirements. By securely connecting on-premises networks to AWS, organizations can meet these standards while protecting privacy and integrity.
- Organizations frequently use a hybrid architecture that combines on-premises infrastructure with cloud resources. Secure communication allows for seamless integration of the two environments, allowing for more efficient operations and data transmission.
Best practices for configuring Site-to-Site VPN
- Implement Strong Encryption: Utilize robust encryption algorithms and security protocols to safeguard VPN traffic from unauthorized access.
- Enable Monitoring and Logging: Monitor VPN connections and log performance metrics to promptly identify and address any issues that may arise.
- Implement Redundancy: Set up multiple VPN connections across different availability zones or regions to ensure high availability and fault tolerance.
- Regularly Review and Update Settings: Continuously review and update VPN settings, routing tables, and security groups to align with evolving network requirements and adhere to best security practices.
- Ensure Compliance: Regularly audit VPN configurations to ensure compliance with security standards and regulatory requirements, maintaining a secure and compliant network environment.
Use cases for Site-to-Site VPN
- Branch Office Connectivity: Connect branch offices to central data centers or cloud resources securely, allowing remote offices to access corporate resources and applications.
- Partner Network Integration: Facilitate secure communication and data exchange between partner networks and your organization’s network, enabling collaboration while maintaining data confidentiality.
- Hybrid Cloud Environments: Integrate on-premises infrastructure with cloud services seamlessly, enabling hybrid architectures for efficient resource utilization and scalability.
- Remote Worker Access: Provide secure access for remote workers to corporate networks and resources, ensuring data security and compliance with remote work policies.
- Disaster Recovery: Establish secure connections for disaster recovery purposes, allowing data replication and backup between on-premises and cloud environments for business continuity.
Steps for Setting Up an AWS Site-to-Site VPN
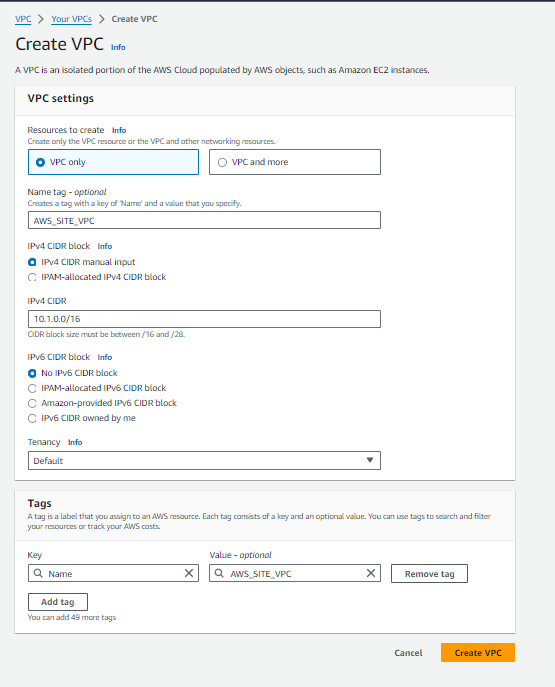
Step#1:Create VPC in Mumbai Region
In the Mumbai region, we have set up a Virtual Private Cloud (VPC) named ‘AWS_SITE_VPC‘ with the CIDR block ‘10.1.0.0/16‘.”
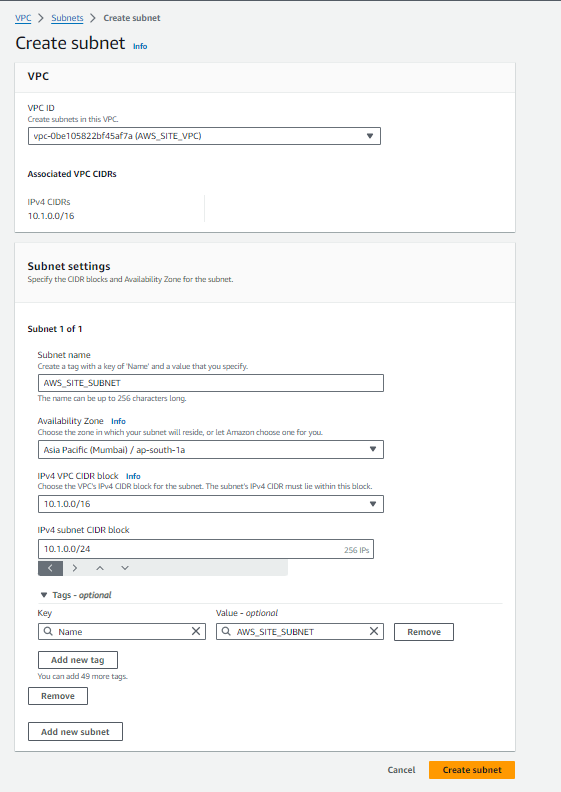
To create a subnet within our VPC ‘AWS_SITE_VPC’ in the Mumbai region (ap-south-1a), follow these steps:
- Name of the Subnet: AWS_SITE_SUBNET
- VPC Name: AWS_SITE_VPC
- Availability Zone: ap-south-1a
- IPv4 CIDR Block: 10.1.0.0/16
- VPC CIDR Block: 10.1.0.0/24″
To enable internet connectivity for our VPC ‘AWS_SITE_VPC‘ in the Mumbai region, follow these steps:
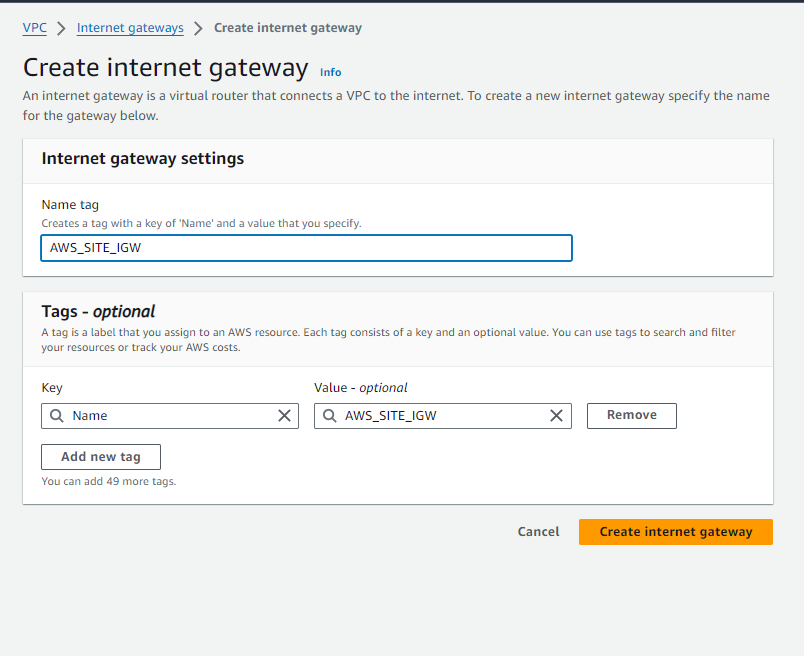
- Select ‘Internet Gateway‘ from the VPC dashboard and click on ‘Create Internet Gateway‘.
- Enter the following details:
- Name: AWS_SITE_IGW
- Click on ‘Create Internet Gateway’.
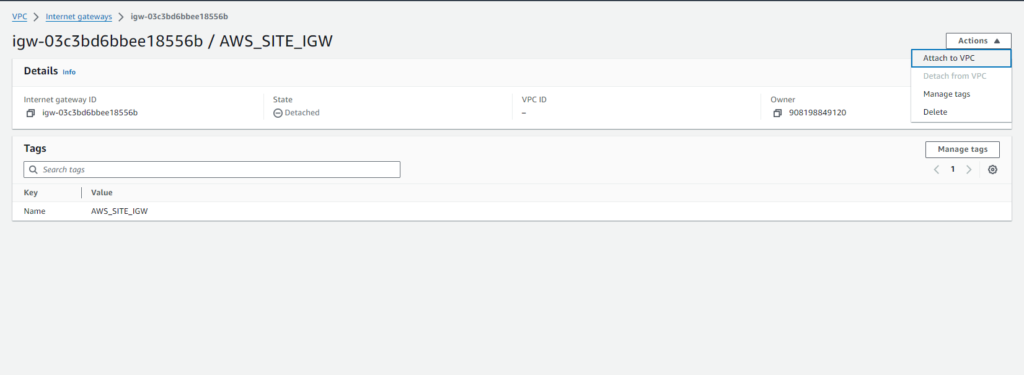
- Next, attach the Internet Gateway to the VPC:
- Select the Internet Gateway ‘AWS_SITE_IGW‘.
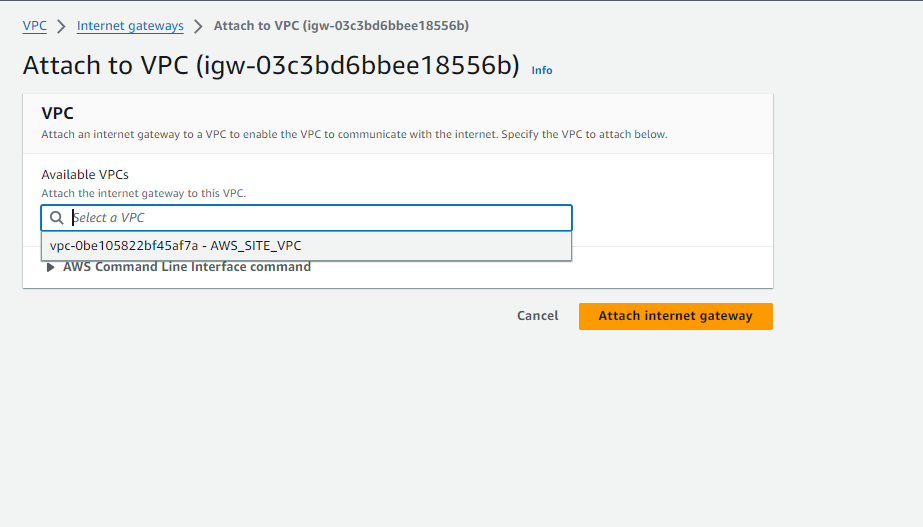
- Click on ‘Actions’ and choose ‘Attach to VPC‘.
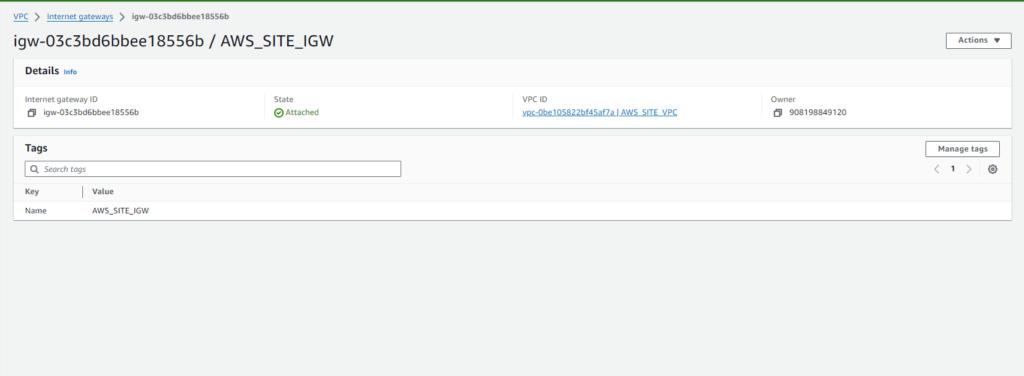
- Select ‘AWS_SITE_VPC‘ as the VPC to attach the Internet Gateway to.
- Confirm the attachment.
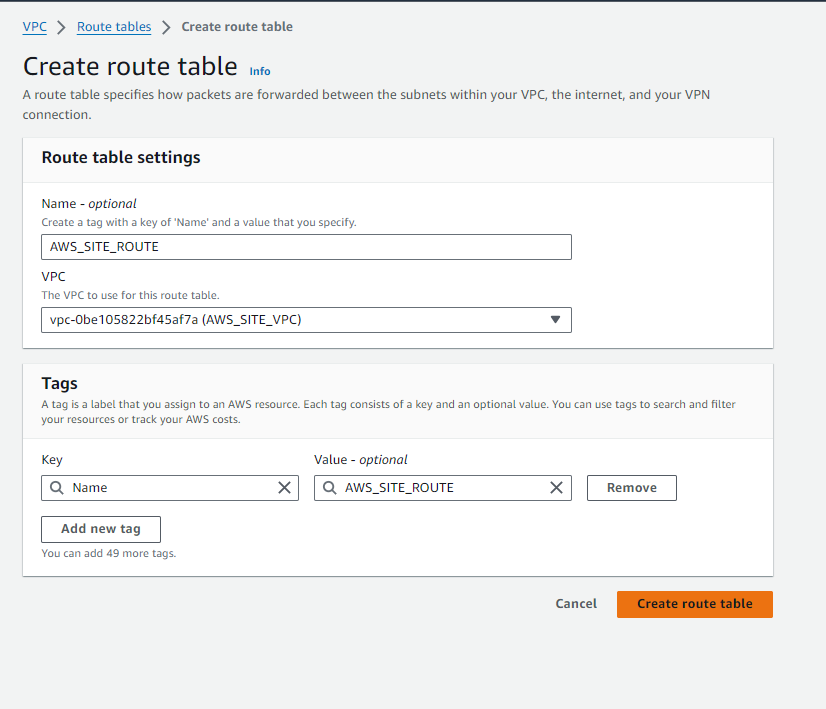
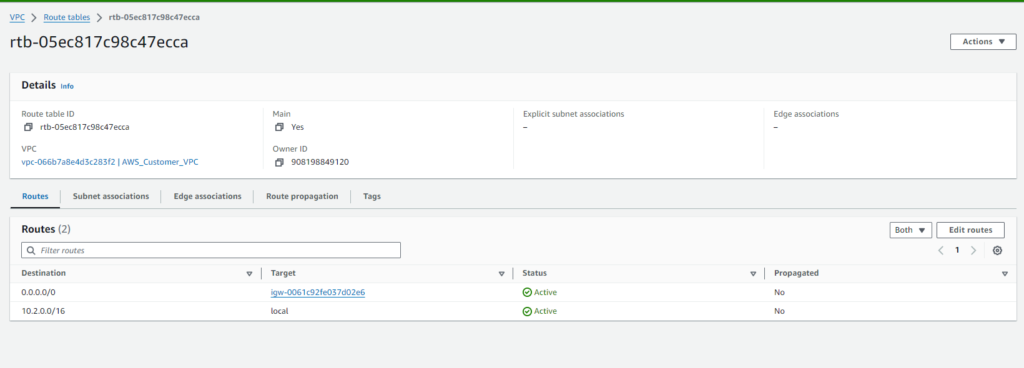
To manage routing within our VPC ‘AWS_SITE_VPC‘ in the Mumbai region, let’s create and configure a route table:
- Navigate to the Route Tables section in the VPC dashboard.
- Click on ‘Create Route Table‘.
- Enter the following details:
- Name: AWS_SITE_ROUTE
- VPC: AWS_SITE_VPC
- Click on ‘Create Route Table‘.
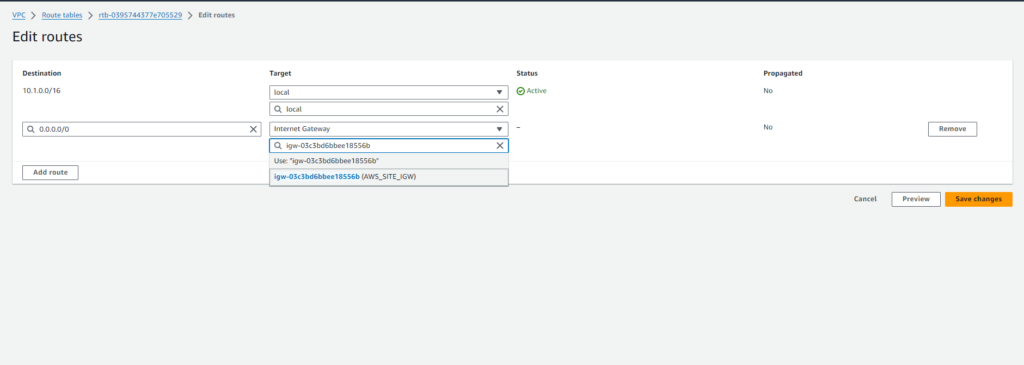
Now, let’s edit the routes in the route table to direct traffic:
- Select the route table ‘AWS_SITE_ROUTE‘.
- Click on ‘Routes‘ tab.
- Click on ‘Edit routes‘.
- Add a new route with the following details:
- Destination: 0.0.0.0/0
- Target: Internet Gateway (select the Internet Gateway associated with your VPC).
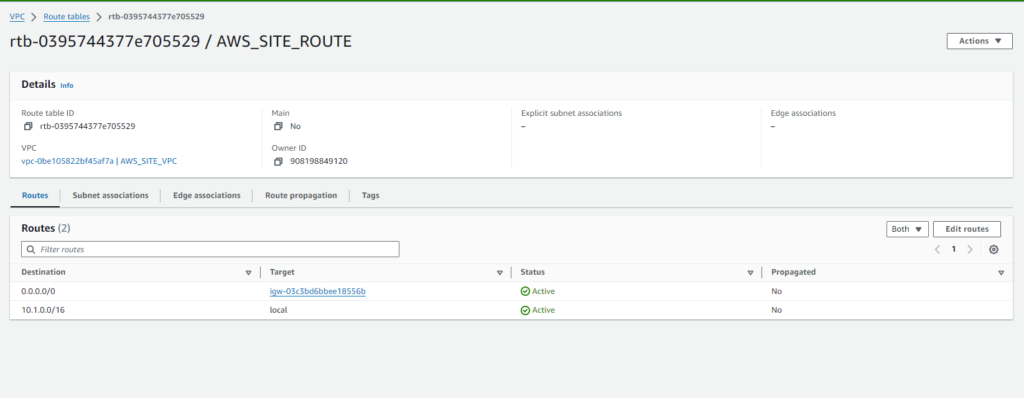
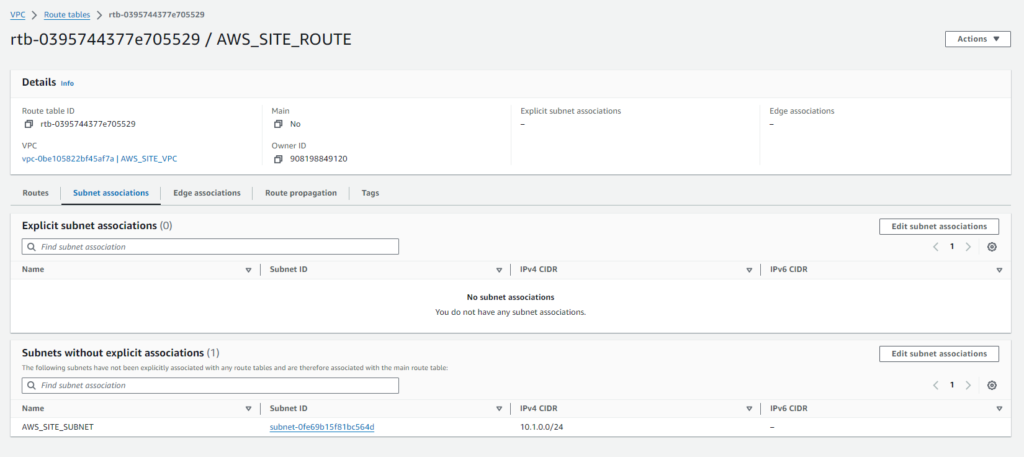
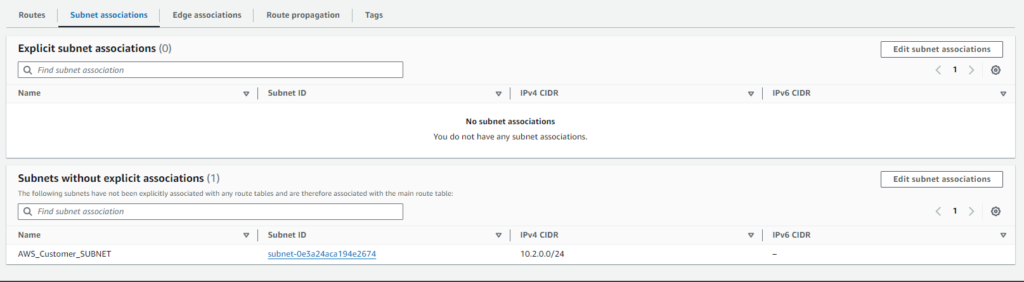
Next, associate the route table with a subnet and ensure proper association:
- Click on ‘Subnet Associations‘ tab.
- Click on ‘Edit Subnet Associations‘.
- Select the subnet(s) within ‘AWS_SITE_VPC‘ that you want to associate with this route table.
- Click on ‘Save’.
Step#2:Create VPC in N.Virginia Region
In the N.Virginia region, we have set up a Virtual Private Cloud (VPC) named “AWS_Customer_VPC‘ with the CIDR block ‘10.2.0.0/16‘.”
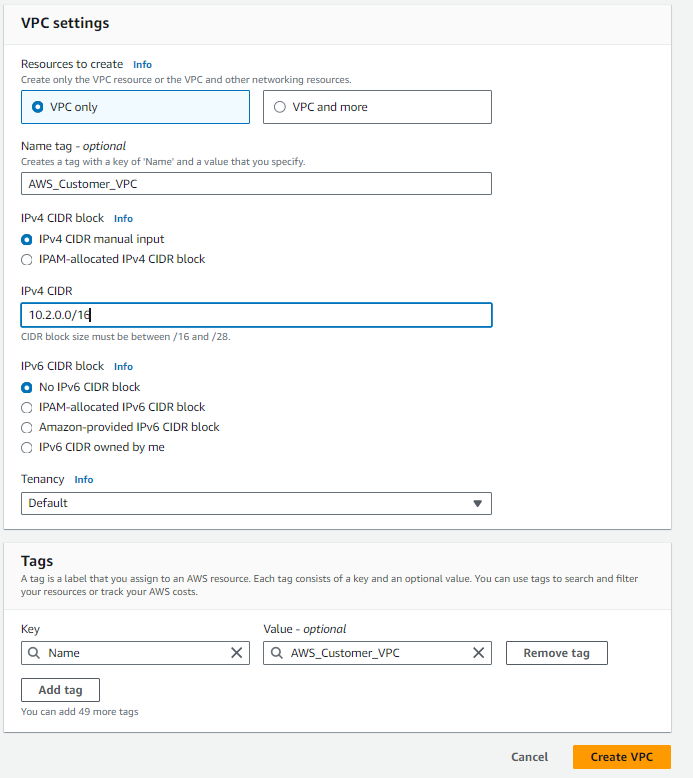
To create a subnet within our VPC ‘AWS_Customer_VPC‘ in the N.Virginia region (us-east-1a), follow these steps:
- Name of the Subnet: AWS_Customer_SUBNET
- VPC Name: AWS_Customer_VPC
- Availability Zone: us-east-1a
- IPv4 CIDR Block: 10.2.0.0/16
- VPC CIDR Block: 10.2.0.0/24″
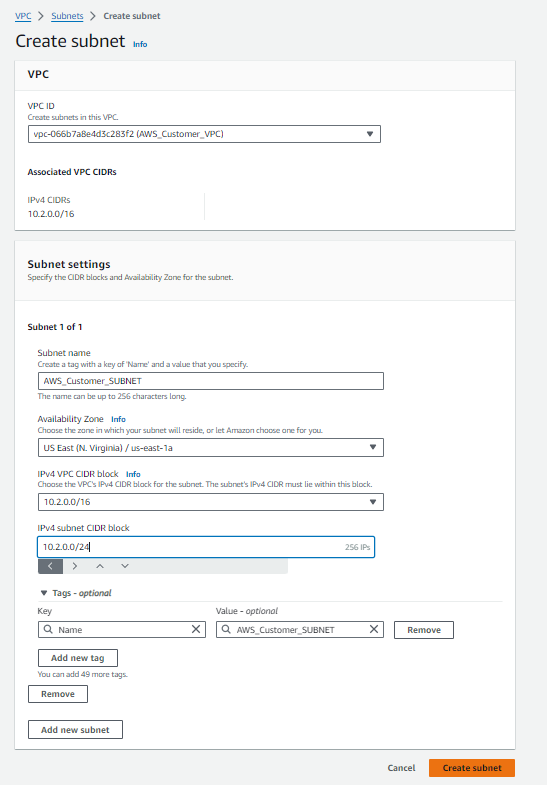
To enable internet connectivity for our VPC ‘AWS_Customer_VPC‘ in the N.Virginia region, follow these steps:
- Select ‘Internet Gateway‘ from the VPC dashboard and click on ‘Create Internet Gateway‘.
- Enter the following details:
- Name: AWS_Customer_IGW
- Click on ‘Create Internet Gateway’.
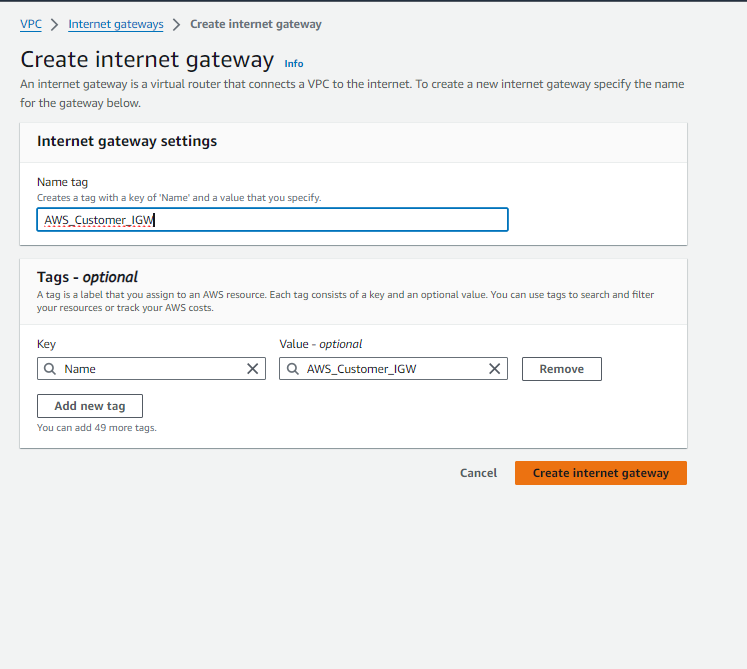
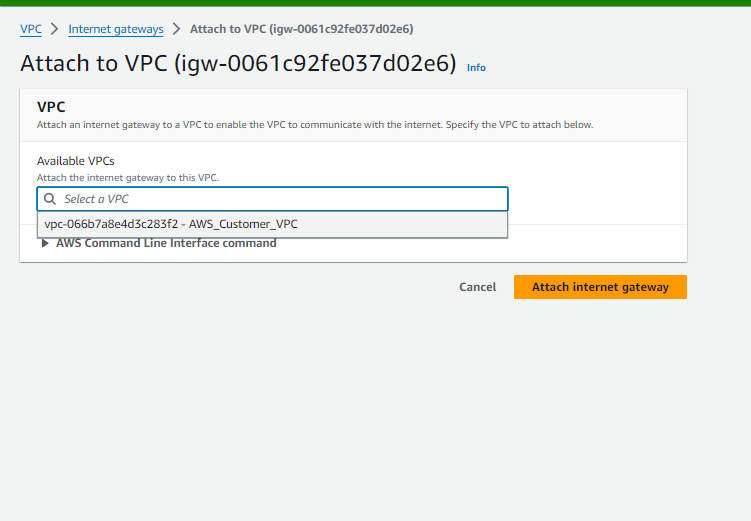
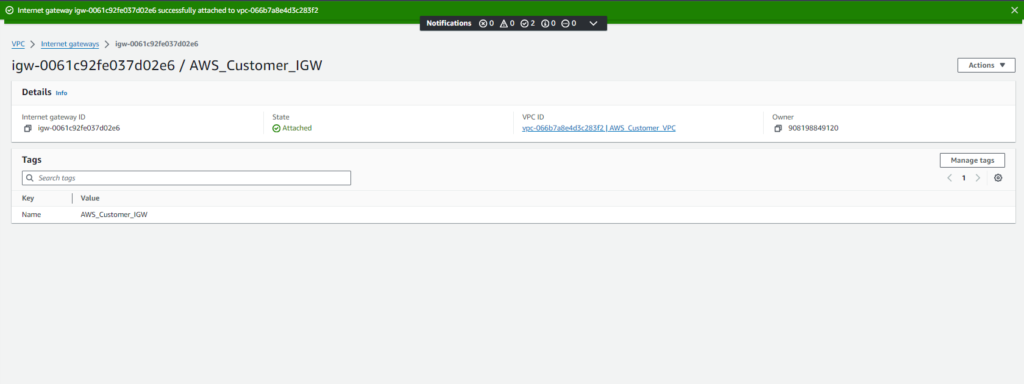
- Next, attach the Internet Gateway to the VPC:
- Select the Internet Gateway ‘AWS_Customer_IGW‘.
- Click on ‘Actions’ and choose ‘Attach to VPC‘.
- Select ‘AWS_Customer_VPC‘ as the VPC to attach the Internet Gateway to.
- Confirm the attachment.
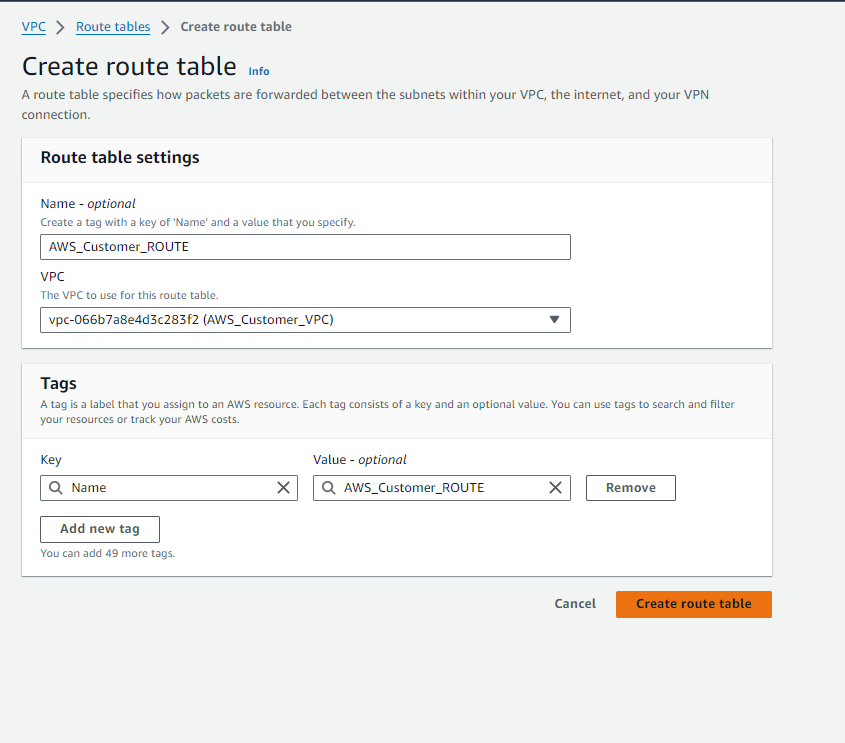
To manage routing within our VPC ‘AWS_Customer_VPC‘ in the N.Virginia region, let’s create and configure a route table:
- Navigate to the Route Tables section in the VPC dashboard.
- Click on ‘Create Route Table‘.
- Enter the following details:
- Name: AWS_Customer_ROUTE
- VPC: AWS_Customer_VPC
- Click on ‘Create Route Table‘.
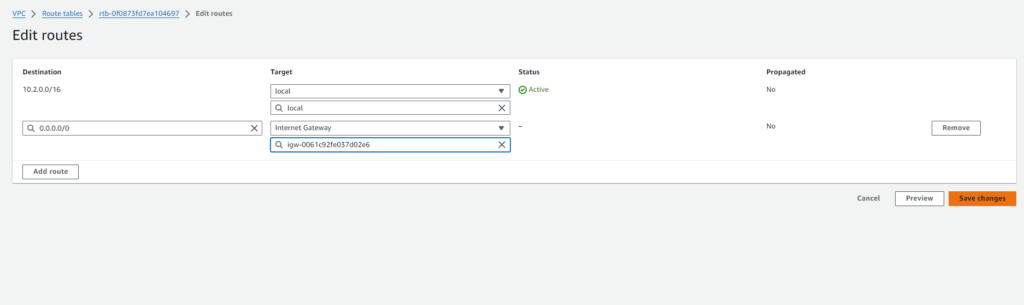
Now, let’s edit the routes in the route table to direct traffic:
- Select the route table ‘AWS_Customer_ROUTE‘.
- Click on ‘Routes‘ tab.
- Click on ‘Edit routes‘.
- Add a new route with the following details:
- Destination: 0.0.0.0/0
- Target: Internet Gateway (select the Internet Gateway associated with your VPC).
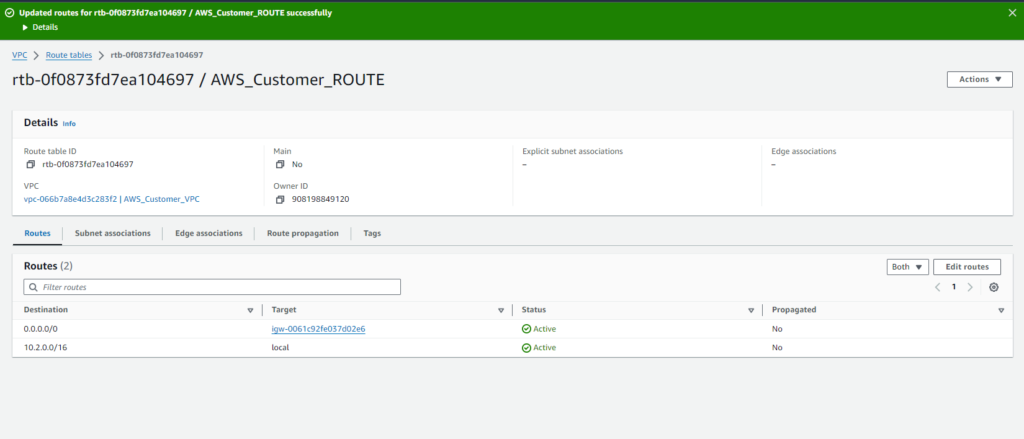
Next, associate the route table with a subnet and ensure proper association:
- Click on ‘Subnet Associations‘ tab.
- Click on ‘Edit Subnet Associations‘.
- Select the subnet(s) within ‘AWS_Customer_VPC‘ that you want to associate with this route table.
- Click on ‘Save’.
Step#3:Launch Amazon Linux Machine in N.Virginia Region
Deploy Amazon Linux instance in N.Virginia region and configure security groups for SSH, TCP, and ICMP access.
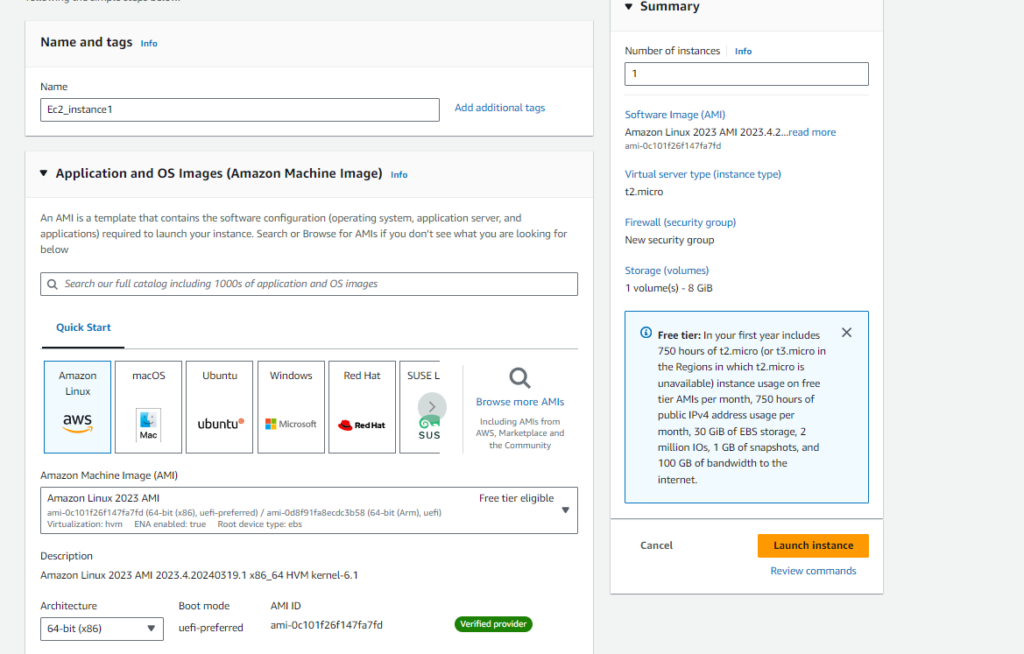
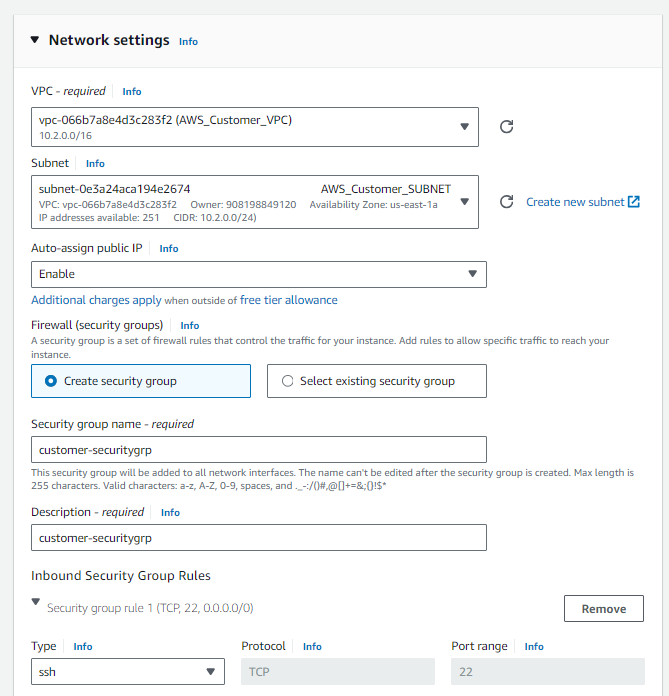
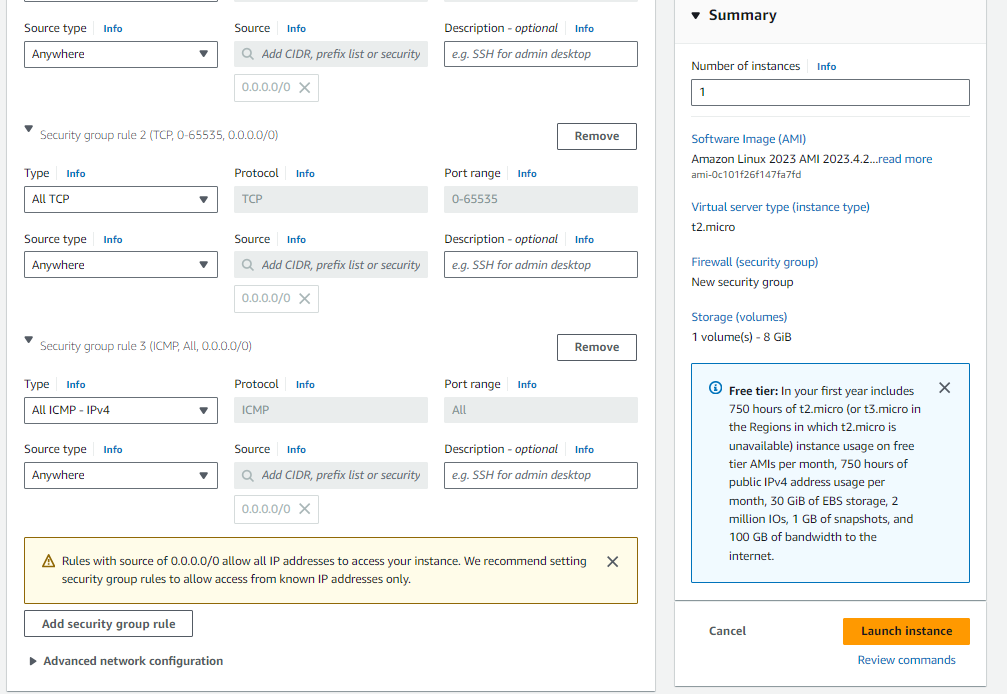
To deploy an EC2 instance in our VPC ‘AWS_Customer_VPC‘ with Amazon Linux as the machine image and t2.micro as the instance type, follow these steps:
- Navigate to the EC2 dashboard and click on ‘Launch Instance’.
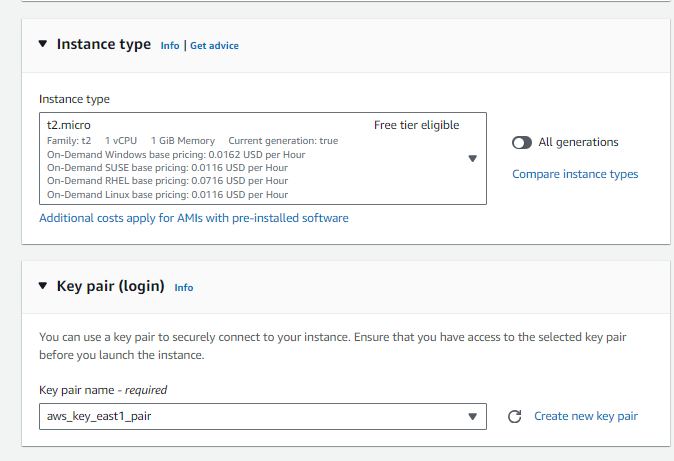
- Choose ‘Amazon Linux‘ as the machine image and ‘t2.micro‘ as the instance type.
- Select ‘AWS_Customer_VPC‘ as the VPC for the instance.
- Enable ‘Auto-assign Public IP‘ for the instance.
- Create a key pair for SSH access.
- Create a security group named ‘customer-securitygrp‘ with the description ‘customer-securitygrp‘.
- Configure the security group with the following rules:
- SSH (port 22) from anywhere
- All TCP from anywhere
- All ICMP (IPv4) from anywhere
Proceed with launching the EC2 instance to set up the desired configuration for your environment.
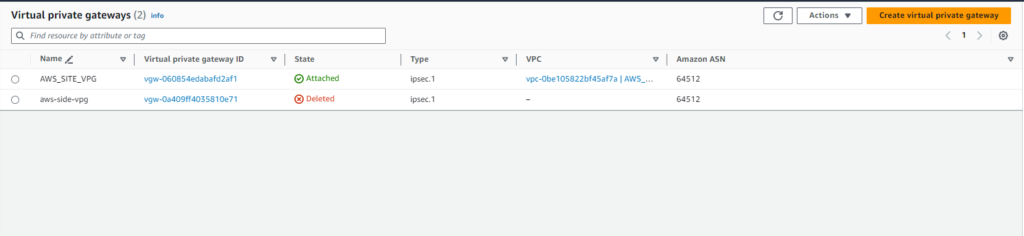
Step#4:Set Up Virtual Private Gateway (VPG) in Mumbai Region
Establish a VPG in the Mumbai region to connect to the AWS VPN network.
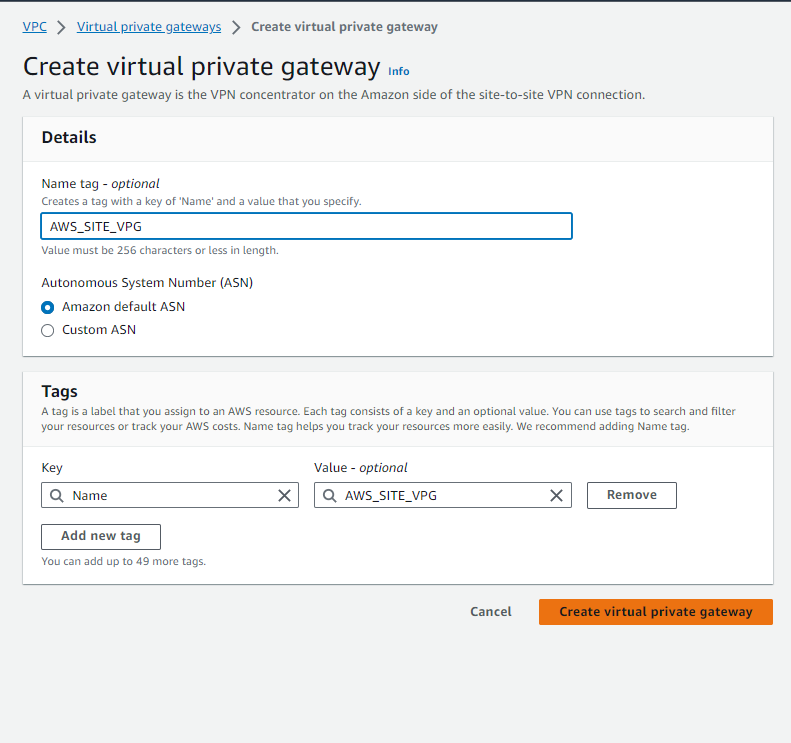
To establish a connection between our VPC ‘AWS_SITE_VPC’ and the AWS VPN network, follow these steps:
- Click on ‘Create Virtual Private Gateway (VPG)’.
- Give the VPG the name ‘AWS_SITE_VPG‘.
- Click on ‘Create’.
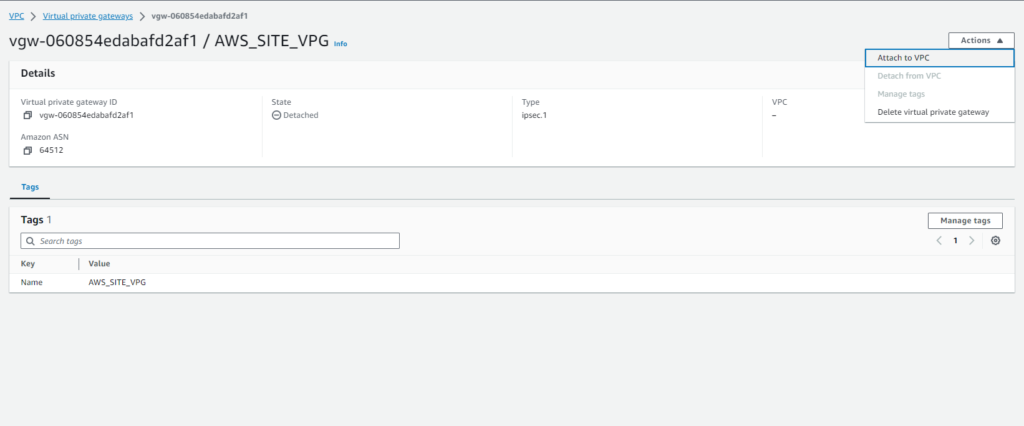
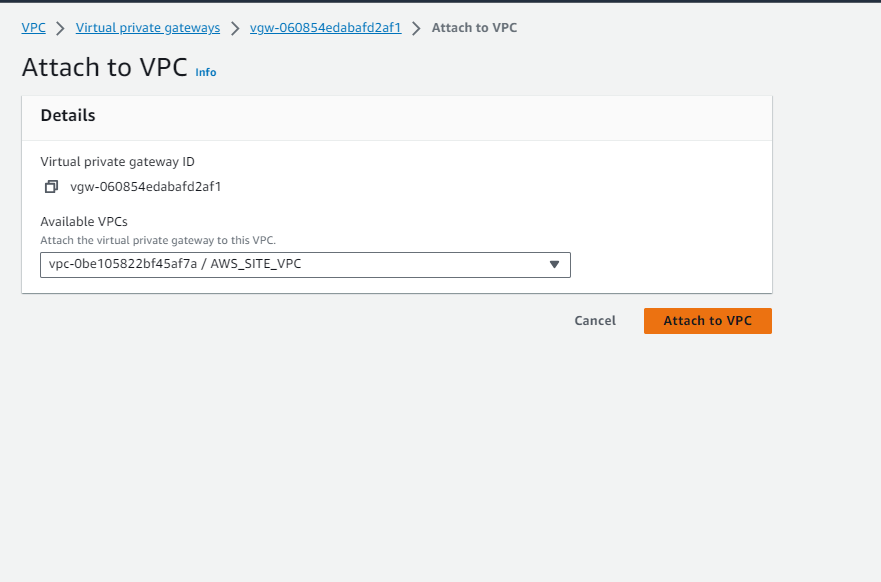
- Next, attach the VPG to the VPC ‘AWS_SITE_VPC‘:
- Select the VPG ‘AWS_SITE_VPG‘.
- Click on ‘Actions’ and choose ‘Attach to VPC’.
- Select ‘AWS_SITE_VPC‘ as the VPC to attach the VPG to.
- Confirm the attachment.
Step#5:Create Customer Gateway (CGW) in Mumbai Region
Configure a CGW in the Mumbai region to represent your on-premises network.
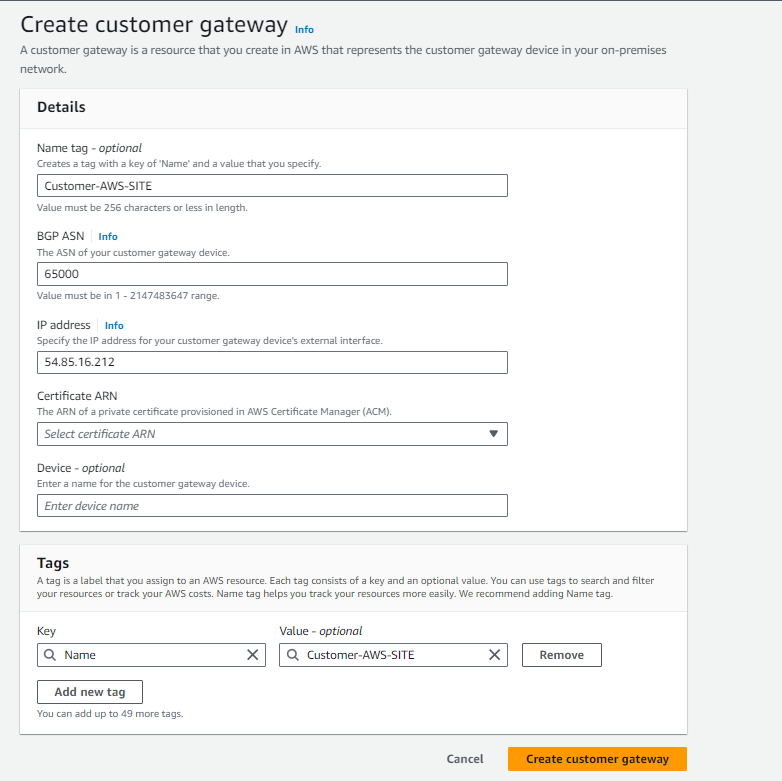
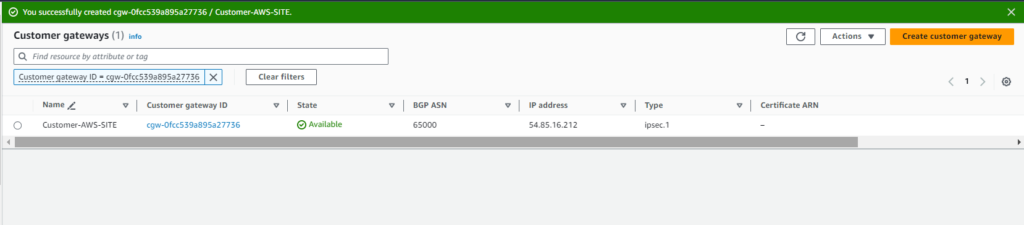
To establish connectivity between our network and AWS, we create a customer gateway ‘Customer-AWS-SITE’ with static routing:
- Navigate to the VPN Connections section in the AWS Console.
- Click on ‘Create Customer Gateway’.
- Enter the following details:
- Name: Customer-AWS-SITE
- Routing: Static (select this option)
- IP Address: [Specify the IP address of the instance launched in the N. Virginia region]
- Keep other settings as default.
- Click on ‘Create Customer Gateway’.
Step#6:Enable Route Propagation in the Mumbai Region
Allow routing between VPCs and on-premises networks by enabling route propagation in Mumbai regions.
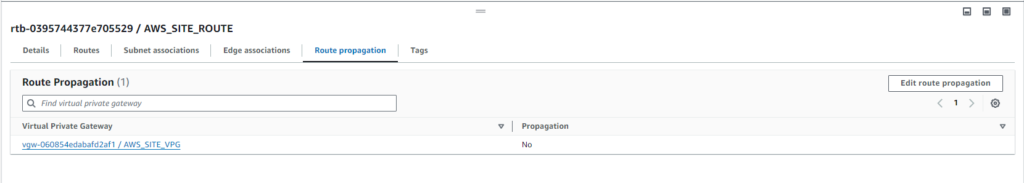
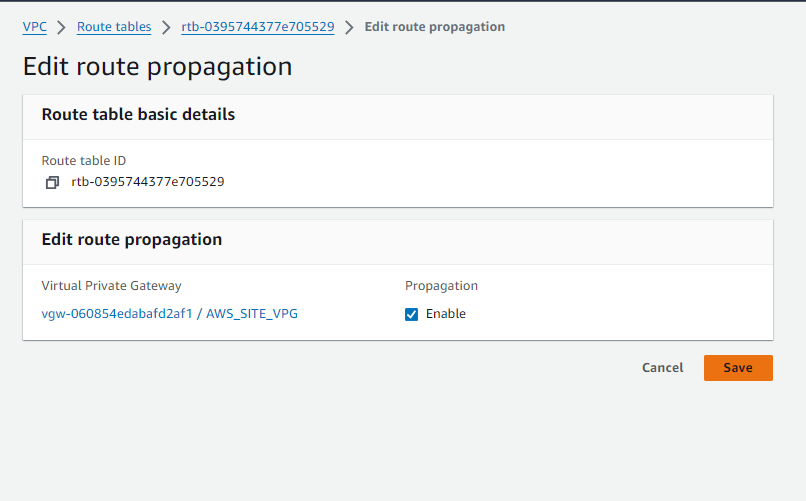
Step#7:Create Site-to-Site VPN Connection in Mumbai Region
Create a Site-to-Site VPN connection in the Mumbai region for secure connectivity between VPCs.
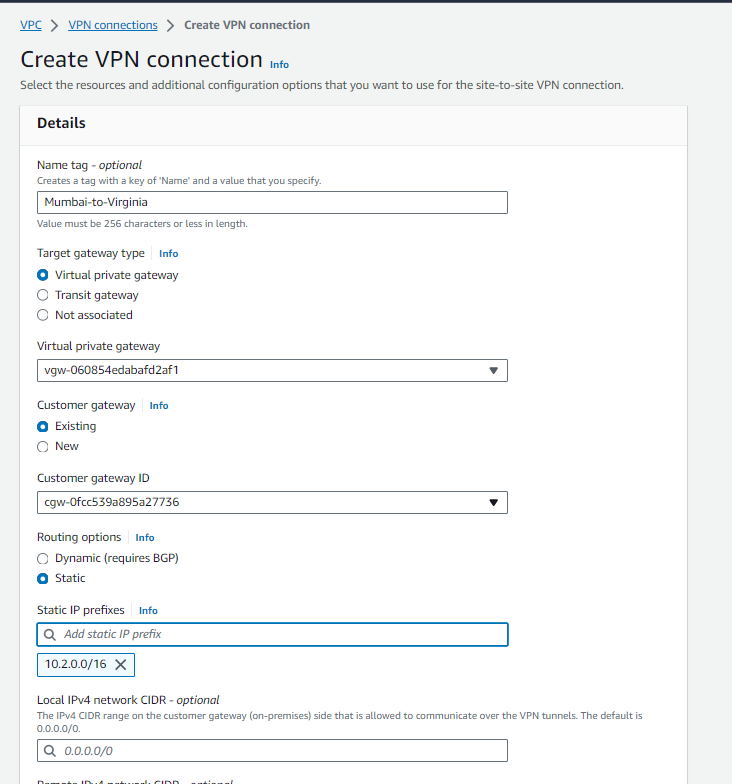
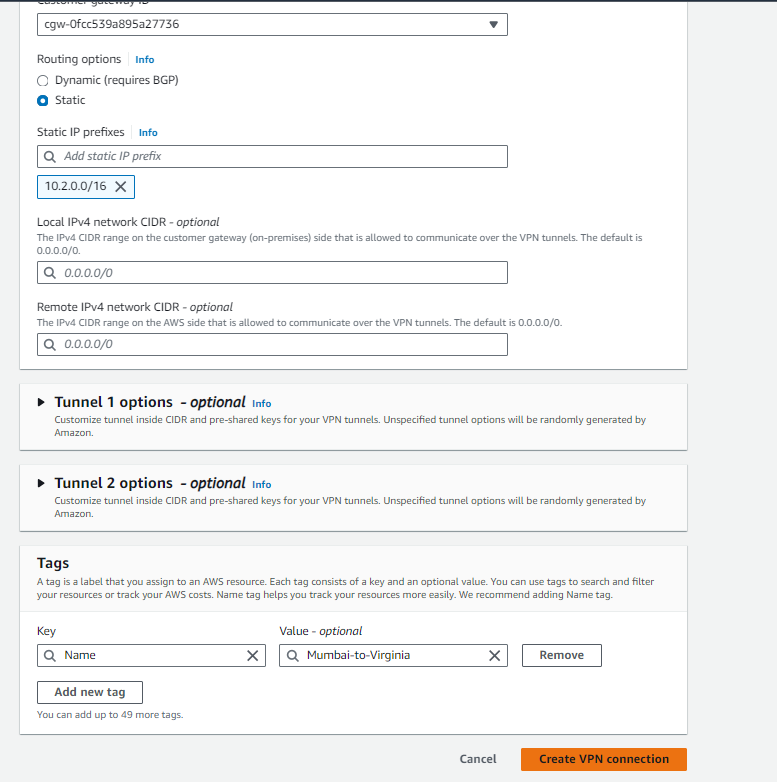
To establish a secure connection between our Mumbai and N. Virginia regions, we create a VPN connection named ‘Mumbai-to-Virginia’:
- Navigate to the VPN Connections section in the AWS Console.
- Click on ‘Create VPN Connection’.
- Enter the following details:
- Name: Mumbai-to-Virginia
- Target: Virtual Private Gateway (select the appropriate VPG)
- Customer Gateway: [Select the previously configured Customer Gateway]
- Routing Options: Static (select this option)
- Static IP Prefix: 10.2.0.0/16
- Click on ‘Create VPN Connection’.
This setup establishes a VPN connection using static routing, ensuring secure communication between our Mumbai and N. Virginia regions.”
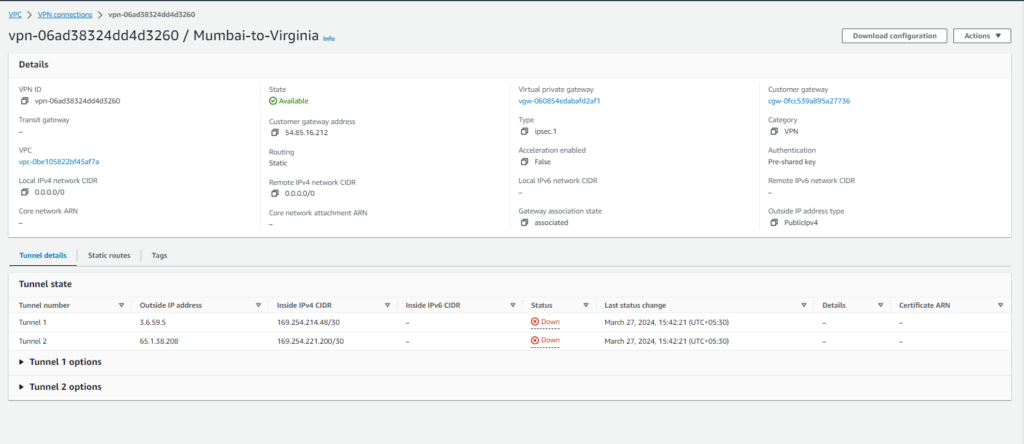
Step#8:Download VPN Configuration
Obtain the Site-to-Site VPN configuration from AWS for setting up your on-premises VPN device.
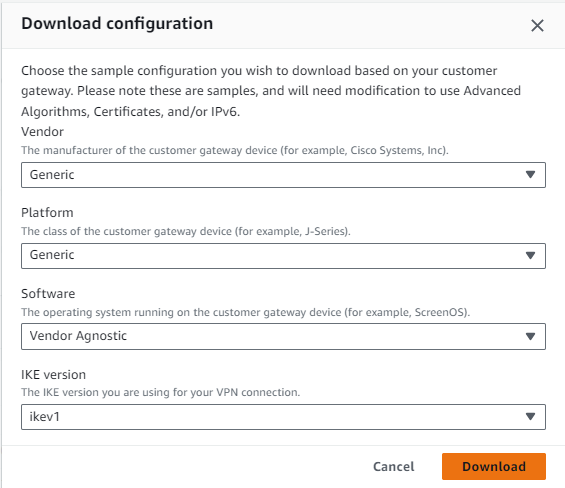
Configuration is opened on Notepad
Step#9:Access EC2 Instance launced in N.Virginia Region
Use Mobaxterm/Putty to access the EC2 instance in the N. Virginia region, accessible via the VPN connection.
What is libreswan?
Libreswan is an open-source implementation of the IPsec (Internet Protocol Security) protocol suite for Linux-based systems. It provides secure communication over IP networks by encrypting and authenticating data packets.
Enter the below commands After Connecting with Ec2 instance:-
- Change to root user:
sudo su
- Install Libreswan:
yum install libreswan -y
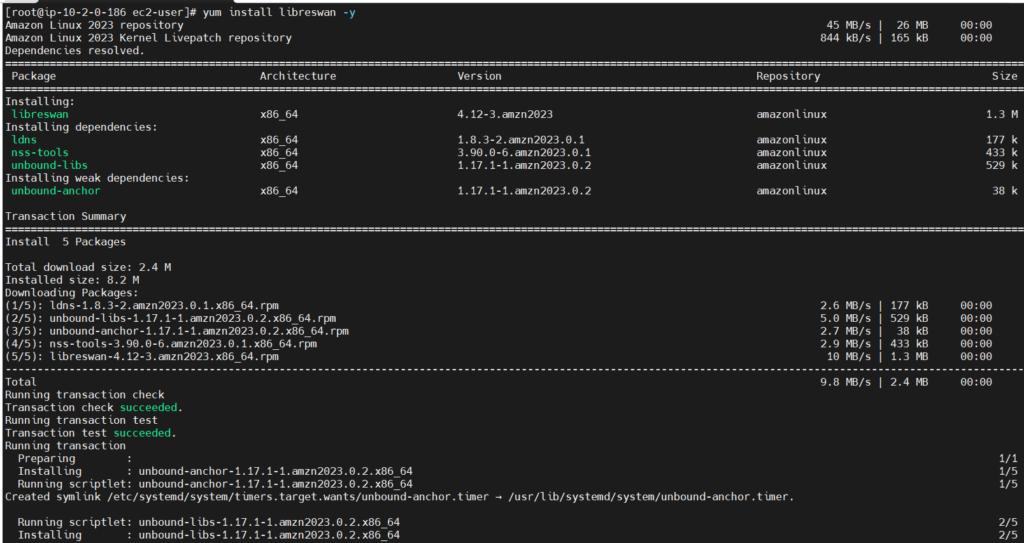
- Modify /etc/ipsec.conf:
Ensure the following line is uncommented or add it if not present:
vi /etc/ipsec.conf
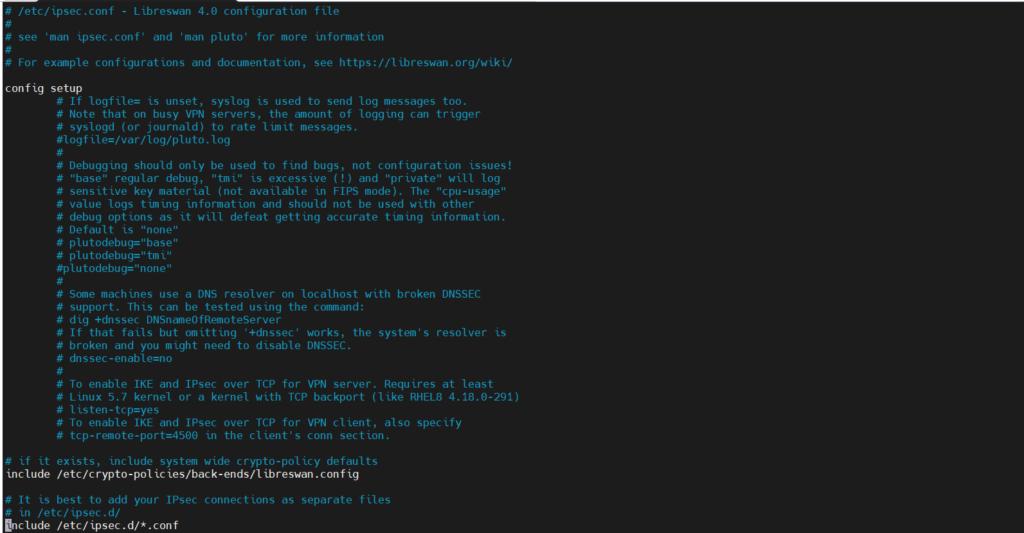
include /etc/ipsec.d/*.conf
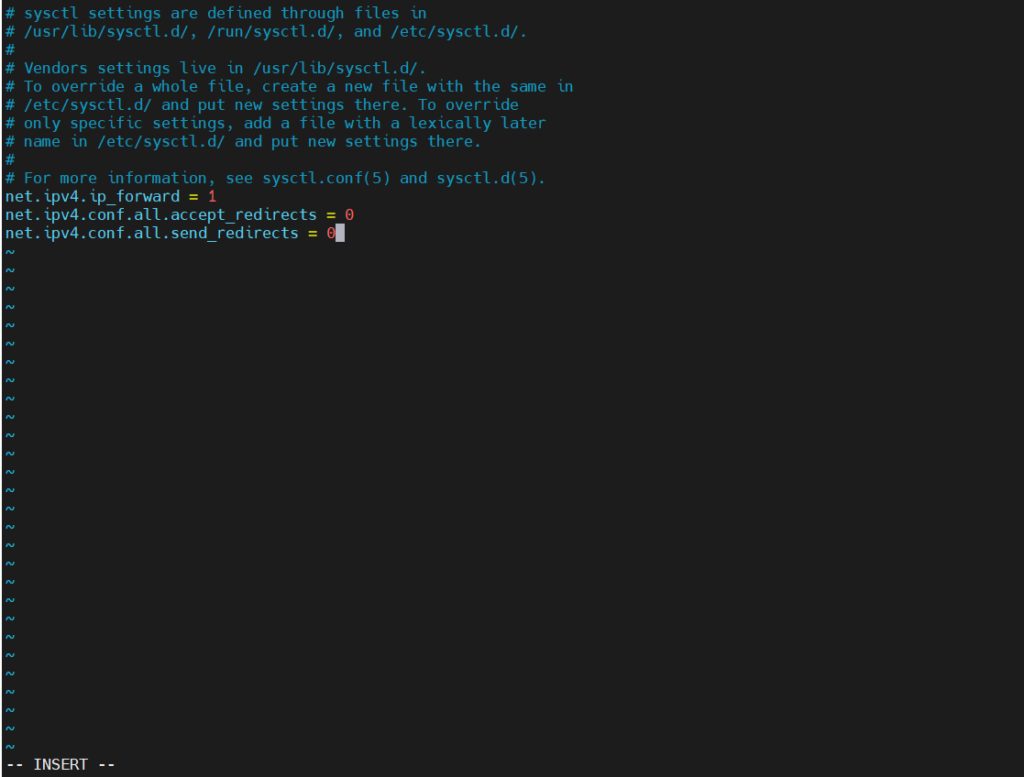
- Update /etc/sysctl.conf:
Edit the /etc/sysctl.conf file and add or modify the following lines:
vi /etc/sysctl.conf
net.ipv4.ip_forward = 1 net.ipv4.conf.all.accept_redirects = 0 net.ipv4.conf.all.send_redirects = 0
- Restart network service:
systemctl restart systemd-networkd
- Create/Edit /etc/ipsec.d/aws-vpn.conf:
vi /etc/ipsec.d/aws-vpn.conf
conn Tunnel1 authby=secret auto=start left=%defaultroute # Assuming this is your local subnet, replace if needed leftid=54.85.16.212 right=3.6.59.5 type=tunnel ikelifetime=8h keylife=1h # Consider stronger options if supported by both sides: # phase2alg=aes256-gcm-sha256 # ike=aes256-gcm-sha256 # keyingtries=%forever keyexchange=ike leftsubnet=10.2.0.0/16 rightsubnet=10.1.0.0/16 dpddelay=10 dpdtimeout=30 dpdaction=restart_by_peer
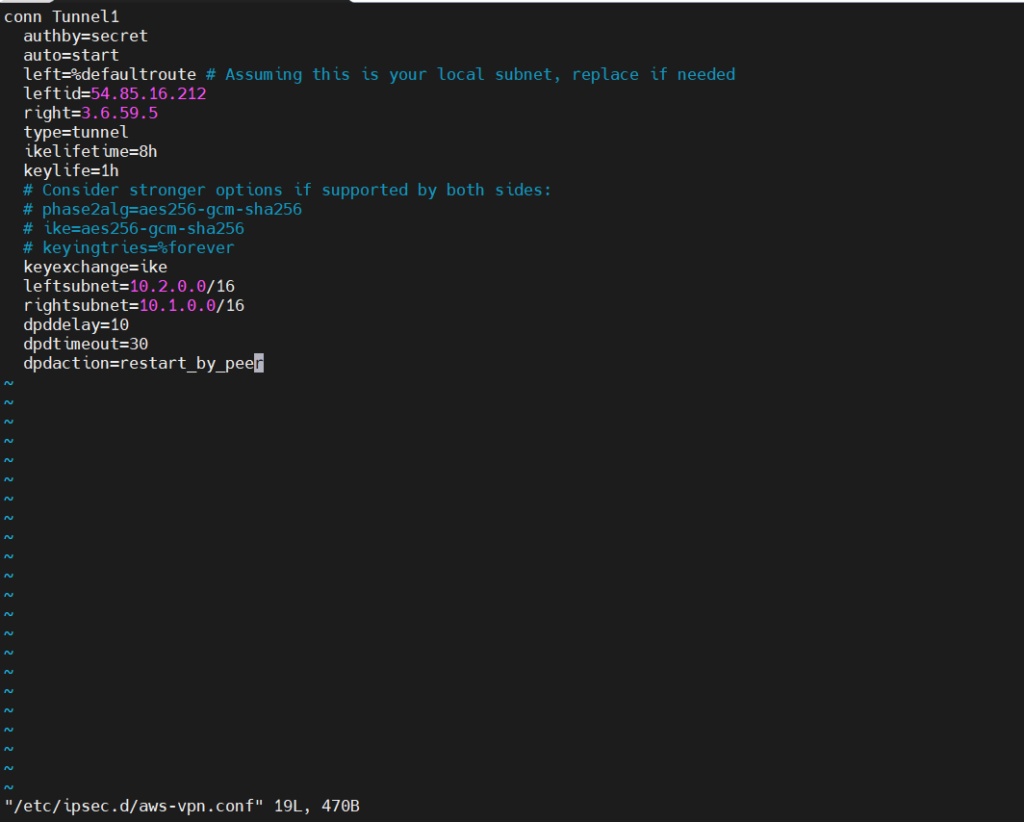
- Create/Edit /etc/ipsec.d/aws-vpn.secrets:
vi /etc/ipsec.d/aws-vpn.secrets
customer_public_ip aws_vgw_public_ip : PSK "shared secret"
54.85.16.212 3.6.59.5: PSK "6hCv4ZehxKhhfb8cNfC4z4NBicyod_W6"
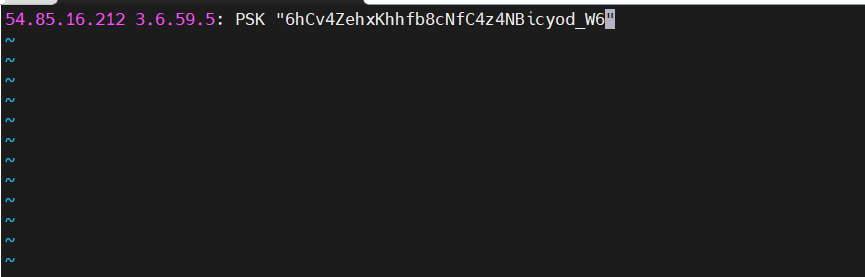
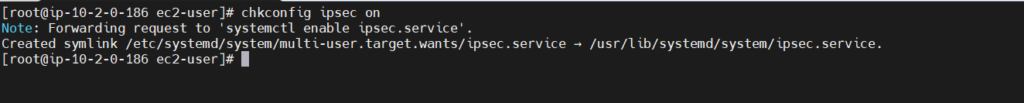
- Commands to enable/start ipsec service:
chkconfig ipsec on
service ipsec start
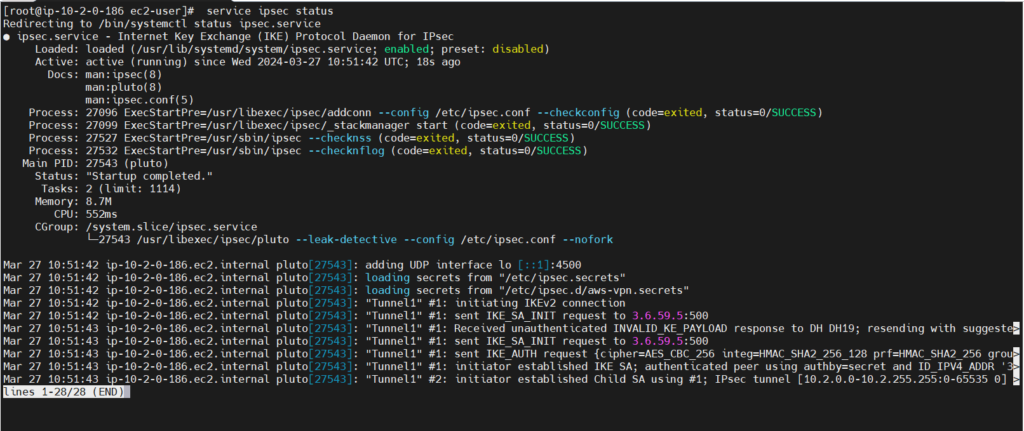
service ipsec status
Step#10:Verify Tunnel Status on AWS Console
Check AWS Console to ensure successful VPN tunnel status, confirming connectivity between VPCs.
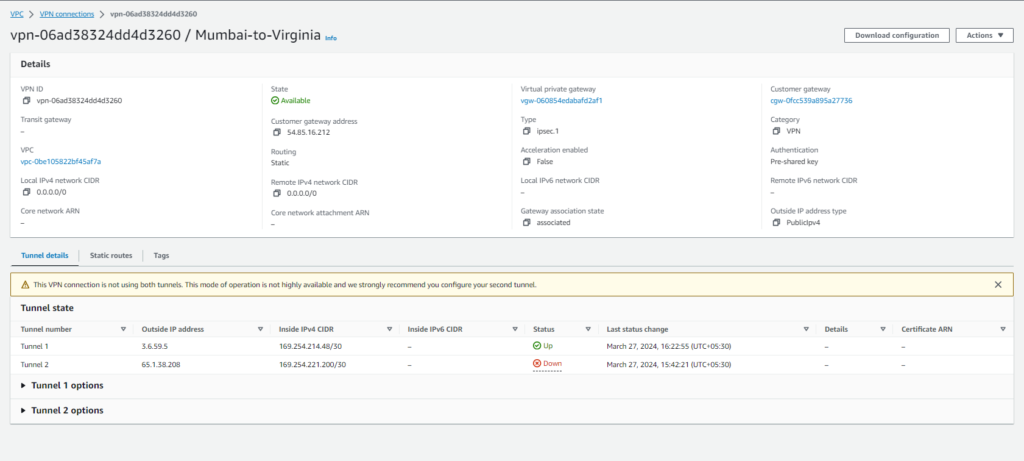
Conclusion:
In conclusion, setting up an AWS Site-to-Site VPN enables secure connectivity between on-premises networks and AWS cloud resources, fostering data protection, regulatory compliance, and seamless hybrid architecture integration for enhanced business operations.
Reference:-
For reference visit the official website .
Any queries pls contact us @Fosstechnix.com.
Related Articles:

