In this article we will discuss Terraform State File Corruption Recovery with Examples.
The terraform.tfstate file plays a crucial role in Terraform by keeping track of the current state of your infrastructure. When this file is corrupted or lost, Terraform can no longer accurately manage your resources, often leading to infrastructure drift—a mismatch between your actual infrastructure and what’s defined in your configuration files.
This kind of issue can arise from several causes, including:
- Accidental overwrites or deletions
- Conflicts during Git merges
- Manual edits to the state file
- System crashes or Terraform run interruptions
- Misconfigurations in remote backends like S3
Losing access to a valid state file can severely impact your ability to apply, destroy, or update infrastructure safely. In this guide, you’ll learn how to simulate state file corruption and explore various methods to recover or rebuild your Terraform state, ensuring minimal downtime and avoiding unwanted resource changes.
Table of Contents
Simulating State File Corruption (With Remote Backend)
If you’re using S3 remote backend, here’s how you can simulate state file corruption:
⚠️ Warning: Simulating corruption in a production environment is risky and not recommended. Always test these scenarios in a sandbox or non-critical environment to avoid unintended loss or damage to infrastructure. Ensure backups and versioning are in place before experimenting.
Step #1:Find Your State File Key
Usually defined in your main.tf backend block:
terraform {
backend "s3" {
bucket = "<bucket-name>"
key = "env/dev/terraform.tfstate"
region = "ap-south-1"
}
}Step #2:Download the Existing State File
aws s3 cp s3://<bucket-name>/env/dev/terraform.tfstate state.json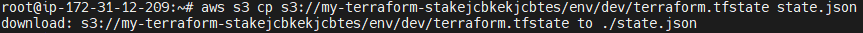
Step #3:Corrupt the State File
echo "this is corrupted state" > state.json
Step #4:Overwrite the Remote State
aws s3 cp state.json s3://<bucket-name>/env/dev/terraform.tfstate
Step #5:Try a Terraform Command
terraform planYou will get an error like:
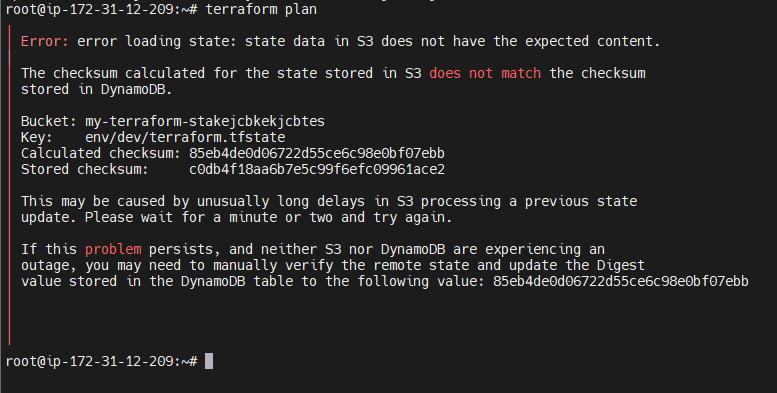
Recovery Methods
#1.Restore From S3 Version History
If S3 versioning is enabled:
a.List the Versions
aws s3api list-object-versions \
--bucket <bucket-name> \
--prefix env/dev/terraform.tfstate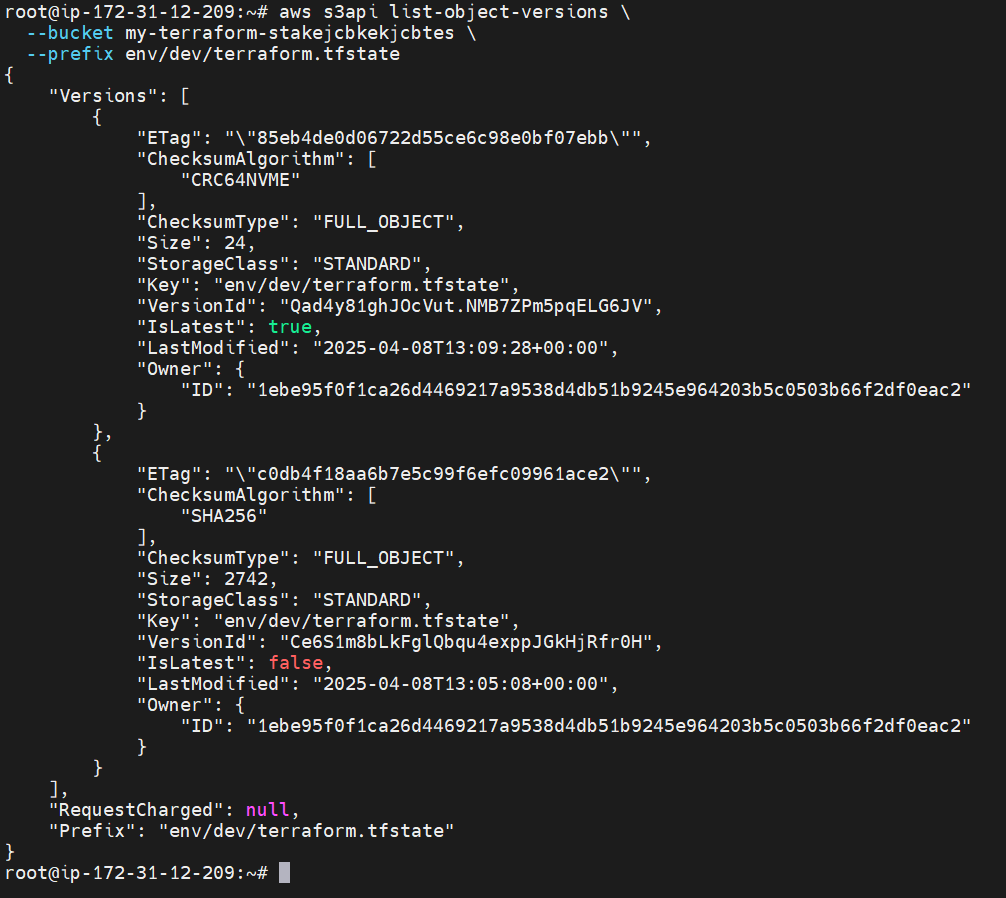
b.Restore the Previous Valid Version
Choose the most recent version with a realistic size (typically over 1 KB) and restore it:
aws s3api copy-object \
--bucket <bucket-name> \
--copy-source my-terraform-states/env/dev/terraform.tfstate?versionId=<PREVIOUS_VALID_VERSION_ID> \
--key env/dev/terraform.tfstate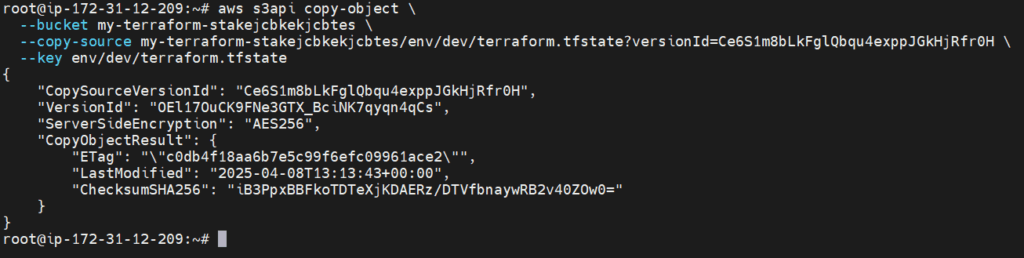
Then run:
terraform plan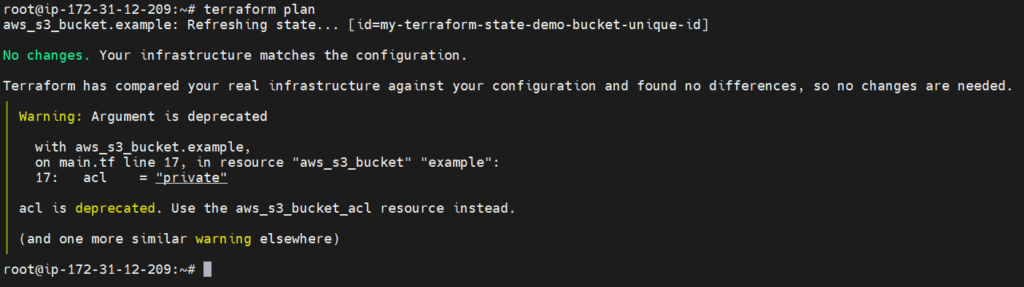
If Terraform complains about a checksum mismatch, update the Digest in your DynamoDB state lock table to match the latest version’s checksum.
#2.Use terraform state pull
If state is not totally broken, you may be able to retrieve the latest remote state:
terraform state pull > backup.tfstate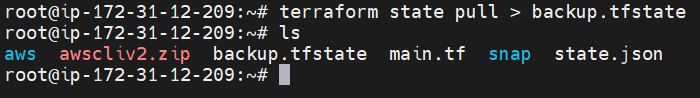
You can recover it later with:
terraform state push backup.tfstate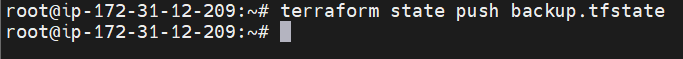
⚠️ Warning: Always open
backup.tfstateand make sure it’s a valid JSON file. If it looks corrupted (e.g., unreadable characters or plain text), do not push it. Instead, use versioning to restore a healthy state.
#3.Use terraform refresh (Cautiously)
This will sync state with real infrastructure. But it doesn’t recreate deleted resources:
terraform refresh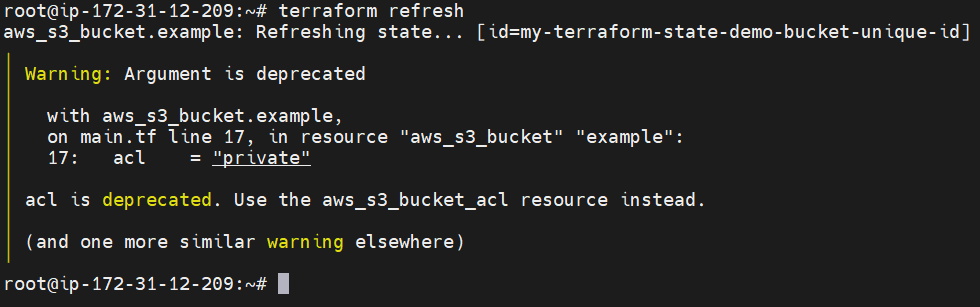
Use this only if you’re sure infrastructure exists and just want to resync.
#4.Manually Rebuild With terraform import
If state is completely lost and recovery is not possible:
terraform import aws_instance.example i-1234567890abcdef0Repeat for all existing resources to rebuild state manually.
Pro Tips for Future Prevention
| ✅ Best Practice | Description |
|---|---|
terraform state pull | Always back up current state before major changes |
| S3 Versioning | Enables rollback to previous state snapshots |
| DynamoDB Locking | Prevents simultaneous writes to remote state |
| Store Remotely | Never store critical state locally in teams |
| CI Backups | Automate backups using CI pipelines or cron |
Conclusion:
Recovering from a corrupted Terraform state file can be challenging, but it’s entirely manageable with the right strategies. Whether you restore a previous version from S3, pull the latest remote state, refresh state from your live infrastructure, or manually import resources—there are multiple ways to regain control.
To avoid future disruptions, it’s essential to adopt best practices like enabling S3 versioning, using DynamoDB for state locking, backing up your state regularly, and never manually editing state files. These preventive steps ensure stability and make recovery much easier in critical situations.
Related Articles:
Terraform State Locking using DynamoDB and S3 Bucket
Reference:
